Bad dates: Criminals weaponise calendar invites to sneak phishing lures past email defences
"The abuse of a popular app demonstrates the evolving sophistication of social engineering threats in the wild."

The next time a calendar invitation drops into your inbox, we'd advise you to look extra carefully at its contents.
It's been alleged that cybercriminals are abusing a Calendar app built by a world-leading tech company to send phishing lures which appear to be purchase notifications.
These booby-trapped messages are sent directly from the tech firm's server, enabling them to bypass spam filters.
As a small publication, we tread extra carefully for legal reasons, so have decided to avoid naming the company involved.
BleepingComputer reported that a reader had been sent a payment receipt for $599 charged against the recipient's account with a well-known online payments service.
This dodgy email included a phone number and asked the recipient to urgently call to settle a large bill.
"Hello Customer, Your [payment] account has been billed $599.00. We're confirming receipt of your recent payment," the email said.
A new threat using old tactics
The “callback” scam that urges recipients to dial a number is familiar. What’s unusual is how it is delivered. The phishing text is placed in the calendar event’s notes field, then shared with an address from another major enterprise email provider controlled by the attackers.
That account appears to be tied to a mailing list, automatically forwarding the invite to multiple targets. Because the original message is sent from the tech firm that cannot be named's servers, the invitation inherits their trusted reputation and has a better chance of reaching inboxes.
Ordinarily, forwarding an external email would cause SPF checks to fail. But the return path is altered so that forwarded messages still pass authentication. This combination of tactics makes the phishing attempt look unusually convincing.
While the lure itself is unremarkable, the abuse of legitimate calendar features and the tech firm’s trusted domains gives the scam an edge, making it harder for recipients - and their spam filters - to spot the fraud.
READ MORE: "Businesses aren’t taking it seriously": Why attackers love phones more than laptops
In comments we've edited slightly to avoid naming the tech firm, Tim Ward, CEO and co-founder of Redflags, said, "The abuse of a Calendar app invites to deliver callback phishing emails disguised as legitimate purchase notifications and sent directly from the tech company's email servers, demonstrates the evolving sophistication of social engineering threats in the wild.
"This attack stands out because the messages appear to come from a trusted source, passing standard security checks like SPF, DMARC, and DKIM, so they are more likely to reach users' inboxes and bypass spam filters.
"By embedding the phishing content inside calendar invites, threat actors exploit both user trust in well-known platforms and technical mechanisms that typically validate genuine messages.
"This trend highlights why organisations must stay vigilant and continue empowering users to question unexpected communications (especially those that try to create urgency around suspicious payments or demand direct contact via phone numbers).
"Technical controls and email filtering are vital, but as attackers increasingly repurpose legitimate workflows for phishing, human defence and security awareness remain crucial to reducing risk.
"Users should be wary of unsolicited calendar invites and payment notifications, even when they appear automated or system-driven, and report or delete anything unexpected. Ultimately, resilience against such threats depends on a blend of up-to-date defences and a proactive cybersecurity culture."
Google's calendar hack warning
Earlier this year, Chinese hackers were caught using Google Calendar to attack the US government.
Google Threat Intelligence Group discovered that a Chinese threat actor called APT41 (or HOODOO to its enemies) cracked into a government website, boobytrapped it and then targeted "multiple other government entities", which have not been identified.
The exploited site was jerry-rigged to deliver malware Google has named “TOUGHPROGRESS”.
READ MORE: Europe's energy systems are frighteningly vulnerable to Russian hybrid attack, EU warns
This payload "took advantage of Google Calendar" for command and control (C2), a technique that enables the bad guys to sneak into cloud services by blending their malicious actions with legitimate activity to avoid detection.
"We assess with high confidence that this malware is being used by the PRC (People's Republic of China) based actor APT41," Google wrote.
"APT41’s targets span the globe, including governments and organisations within the global shipping and logistics, media and entertainment, technology, and automotive sectors."
A date with destiny
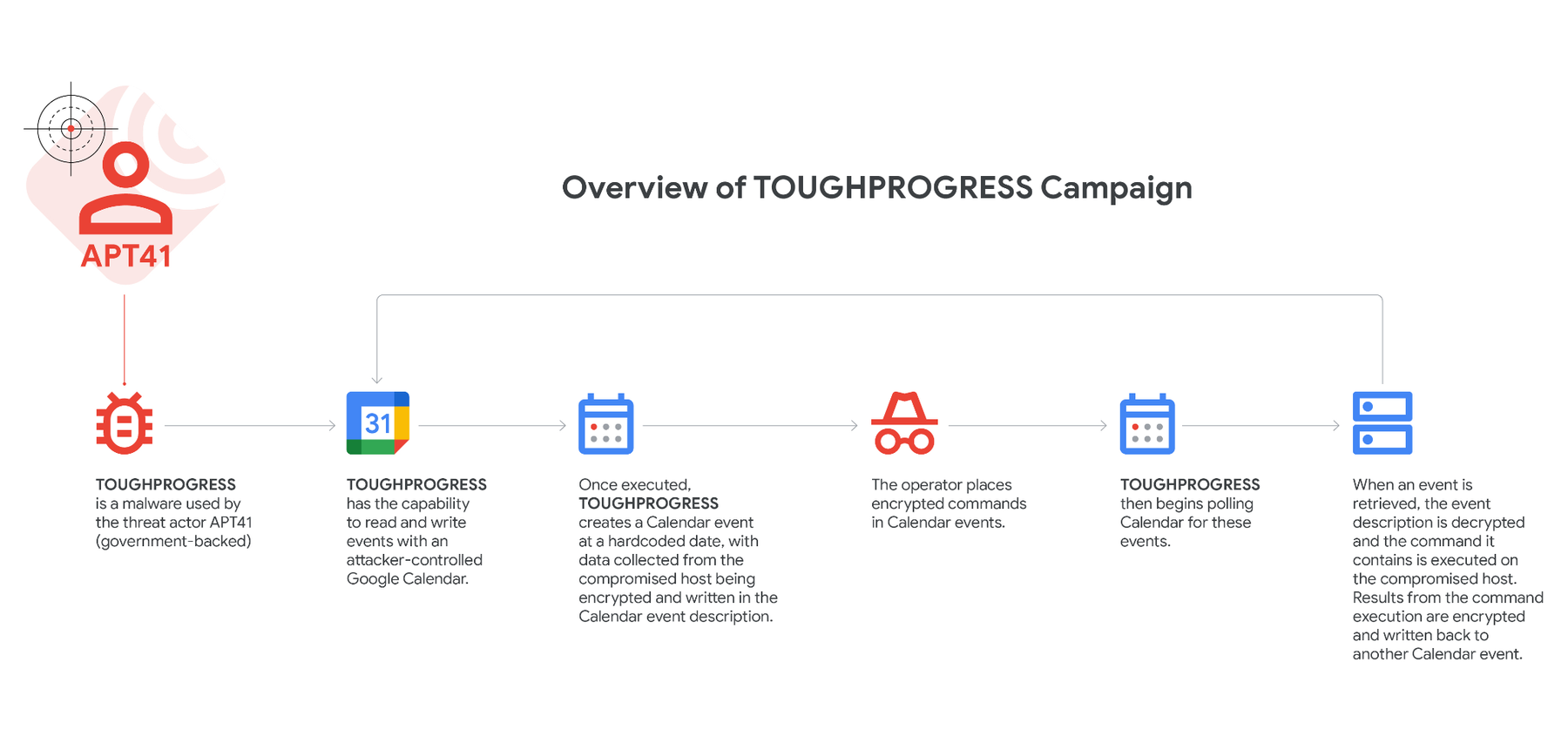
TOUGHPROGRESS can read and write events on an attacker-controlled Google Calendar.
APT41 sent spear-phishing emails containing a link to a ZIP archive stored on the compromised government website. This archive contains an LNK file "masquerading as a PDF" and a directory containing seven JPG images of arthropods.
"When the payload is executed via the LNK, the LNK is deleted and replaced with a decoy PDF file that is displayed to the user indicating these species need to be declared for export," Google wrote.
"This malware has three distinct modules, deployed in series, each with a distinct function," it added. "Each module also implements stealth and evasion techniques, including memory-only payloads, encryption, compression, process hollowing, control flow obfuscation, and leveraging Google Calendar for C2."
These modules are:
PLUSDROP - A Dynamic Link Library (DLL) to decrypt and execute the next stage in memory.
PLUSINJECT - This launches and performs process hollowing, which removes code in an executable file and replaces it with malicious code. In this case, PLUSINJECT targeted a legitimate “svchost.exe” process, pumping it with a final payload.
TOUGHPROGRESS - Executes actions on the compromised Windows host and deploys Google Calendar for C2 command and control.
A payload's progress

Once executed, TOUGHPROGRESS creates a zero-minute Calendar event at a hardcoded date (May 30th 2023). Data is then collected from the compromised host before being encrypted and secretly stored in the Calendar event description. Interestingly and probably coincidentally, Ukraine launched a series of drone attacks against Moscow on this exact date.
Princess Eugenie also gave birth to her son, Ernest George Ronnie, on the same day. But that's even less likely to be relevant.
The malware operator put encrypted commands inside Calendar events on July 30th and 31st 2025 - which are also dates hardcoded into the malware.
TOUGHPROGRESS polls Calendar for these events. When one is retrieved, the event description is decrypted and the command it hides is then executed on the compromised host machine.
Subsequently, the results of the command execution are encrypted and hidden in another calendar event.
Making TOUGHPROGRESS
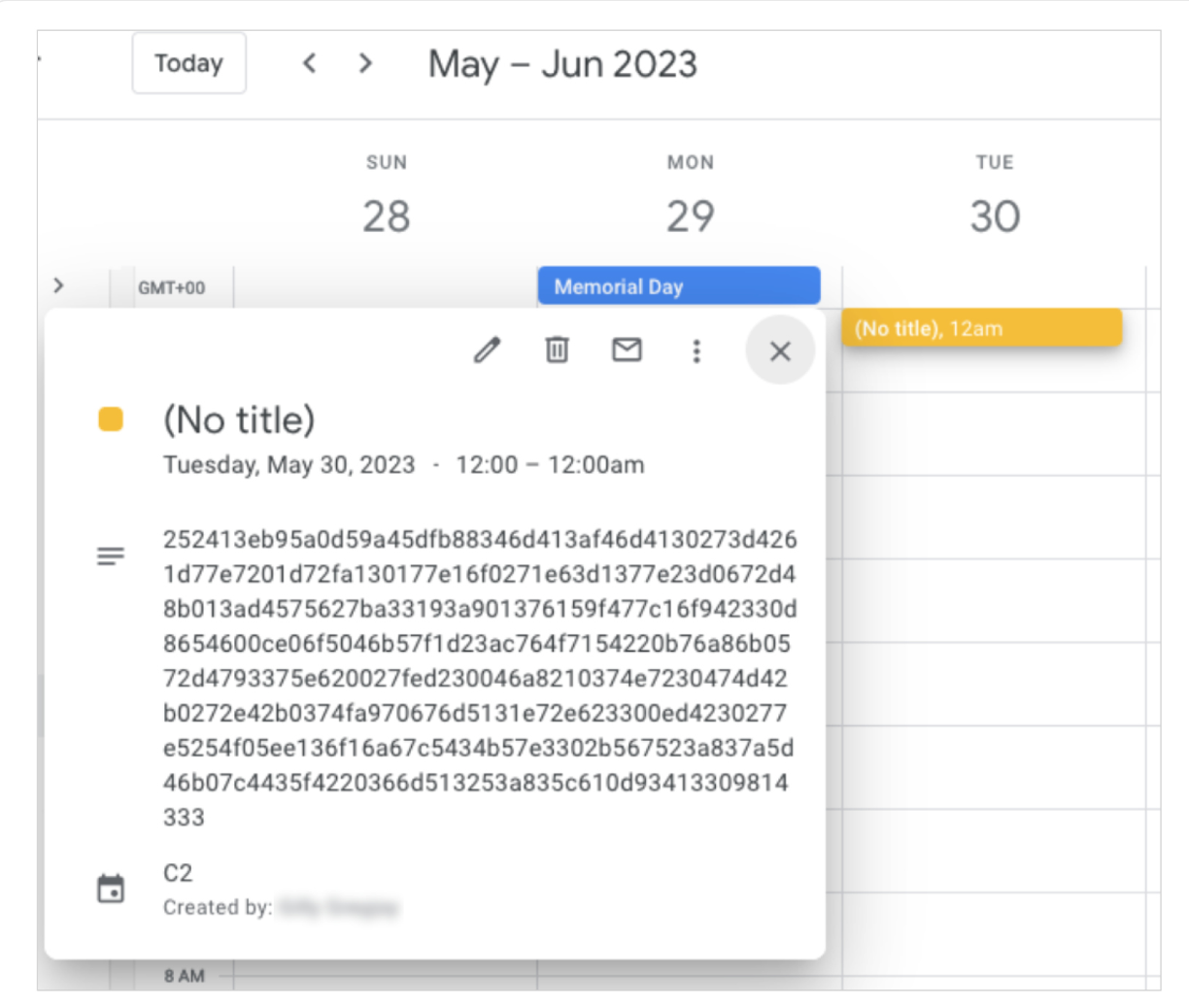
Google reverse engineered the C2 encryption protocol used in TOUGHPROGRESS, to find a 10-byte XOR key that generates a per-message 4-byte XOR key.
It was first compressed with LZNT1 and encrypted it using XOR with a 4-byte (32-bit) key.
A 10-byte header was then created to store metadata. This header was encrypted with the 10-byte XOR key, added to the header of a message. The combined encrypted header and message is then hidden in the Calendar event description, wherein the badness lies.
The Google Threat Intelligence Group has been "actively monitoring and protecting against APT41’s attacks using Workspace apps for several years".
"This threat group is known for their creative malware campaigns, sometimes leveraging Workspace apps," it warned.
Advanced, persistent, threatening
APT 41 lives up to its acronym and is certainly a persistent threat that uses advanced and innovative tactics.
In October 2024, Proofpoint attributed the VOLDEMORT malware campaign to APT41.
And in 2019 and 2020, the FBI indicted five Chinese nationals from APT41 and BARIUM for global cyberattacks, supply chain intrusions, and ransomware operations targeting tech, telecom, and government sectors.
For more information and full TPPs, read Google's full blog.
Do you have a story or insights to share? Get in touch and let us know.




