ChatGPT cracks XLoader malware in record time, "supercharges" human analysts
CheckPoint devises "a new approach to static analysis with AI that turns days of research into hours".

At some point in the future, much of human conflict is likely to involve machines fighting machines (unless they turn on us first).
In cybersecurity, we haven't quite witnessed the dawn of fully autonomous defences capable of operating without a member of our fleshy species at the wheel. Neither have the bad guys got their hands on digital Terminators capable of independent search and destroy operations.
But these scenarios aren't a million miles away and seem closer than ever today, following news that Check Point Research used ChatGPT to crack a notorious piece of malware in hours, rather than days.
Analysts fired up GPT-5 to XLoader 8.0, which Check Point described as "one of the most evasive and persistent information stealers in the wild", using multi-layer encryption, fake domains, and constant updates to avoid detection.
Normally, surgery on this notorious malware would take days of reverse engineering.
But ChatGPT managed the task in hours, identifying encryption layers and decrypted functions, as well as uncovering hidden command-and-control (C2) domains.
ChatGPT vs XLoader
By deploying GenAI, researchers achieved faster IoC extraction and better threat intelligence, promising that their findings would "improve protection for users worldwide."
XLoader has been evolving since 2020 and is a successor to the FormBook malware family. It is capable of stealing data, hiding its code behind multiple encryption layers, and "constantly morphing" to evade antivirus tools and sandboxes.
"Traditional malware analysis is slow and manual—requiring experts to unpack binaries, trace functions, and build decryption scripts by hand," Check Point wrote.
READ MORE: How to stop ghost-brokering and other emerging threats from haunting financial services
"Even sandboxing (running malware in a controlled environment) doesn’t help much, because XLoader decrypts itself only while running and detects when it’s being monitored, keeping its real code hidden.
"This makes XLoader a prime example of modern malware that uses time, complexity, and obfuscation as weapons."
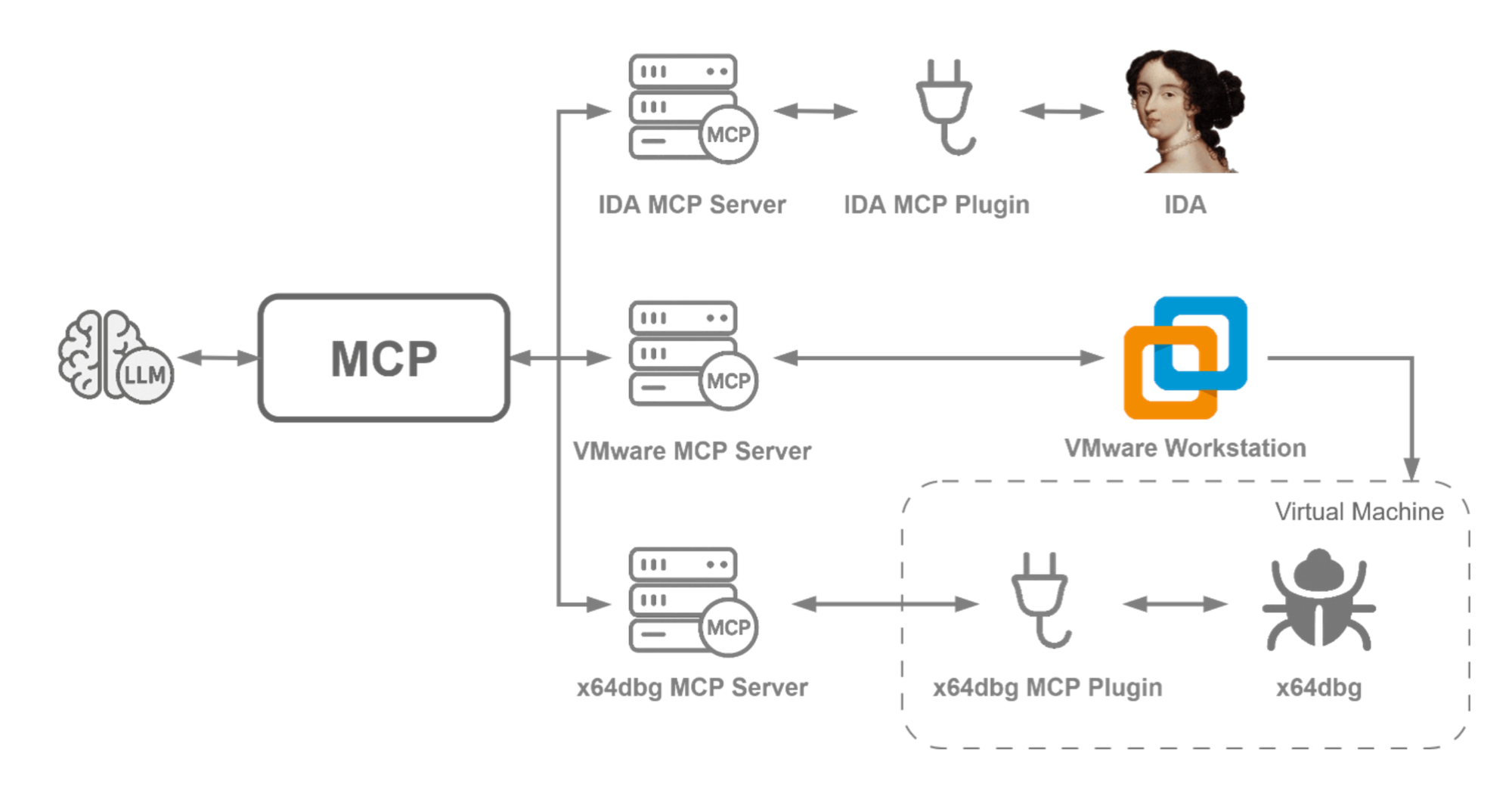
To crack XLoader, analysts used cloud-based static analysis to export data from IDA Pro - a disassembler, decompiler and debugger - then asked the AI to analyse it in the cloud.
"The model identified encryption algorithms, recognised data structures, and even generated Python scripts to decrypt sections of code," Check Point wrote.
Automated malware dissection
Researchers also deployed MCP-assisted runtime analysis, connecting the AI to a live debugger to extract runtime values including encryption keys, decrypted buffers and in-memory C2 data.
"This hybrid AI workflow turned tedious manual reverse engineering into a semi-automated process that’s faster, repeatable, and easy to share across teams," Check Point wrote.
The AI-assisted workflow decrypted more than 100 previously encrypted functions, reconstructing core code for immediate inspection.
It uncovered a trio of "complex decryption schemes" using modified RC4 algorithms and XOR markers. and automatically deobfuscated Windows API calls hidden behind custom hashing.
READ MORE: Agentic AI is facing an identity crisis and no one knows how to solve it
By peeling back multiple layers of Base64 and RC4 encoding, the system exposed 64 command-and-control domains tied to the real attacker infrastructure. It also revealed a novel sandbox-evasion technique - a “secure-call trampoline” that re-encrypts code on the fly to evade monitoring tools.
Check Point added: "In short, AI helped unpack how XLoader hides, communicates, and protects itself, crucial insights for improving detection and prevention. These findings directly strengthened our threat intelligence feeds, allowing Check Point protections to update faster and more accurately."
Will AI replace human cybersecurity analysts?
Not today, Check Point insisted.
"AI doesn’t replace malware analysts. Rather, it supercharges them. Tasks that once took days can now be completed in under an hour. Anyone with the exported dataset can re-run the AI workflow and validate results.
"Automation frees analysts to focus on high-level behaviours—how malware spreads, steals, and evolves. Faster indicators of compromise (IoCs) extraction shortens the time between threat discovery and protection rollout.
"Generative AI is now a powerful tool for incident response, reverse engineering, and threat hunting.
"Malware authors will likely adapt to AI-driven analysis, but the defensive advantage is clear: AI allows defenders to respond in near real time to complex, encrypted threats like XLoader."
This statement reflects broader industry sentiment, which suggests that AI will not replace humans but augment and enhance their work.
Many security firms have made similar claims, forecasting a bright future where AI handles routine tasks, alleviating alert fatigue, while real-life analysts are freed to enjoy the sunlit uplands of life without boring, manual, and repetitive tasks.
Let's hope this turns out to be true!




