China escalates cyberwar on Taiwan, aims to "paralyze" critical infrastructure
Taiwanese intelligence agency warns of a dramatic uptick in intrusions designed to "undermine public morale".

China’s “cyber army” has stepped up its attacks against Taiwan, targeting critical infrastructure including hospitals, food production, energy facilities and water resources.
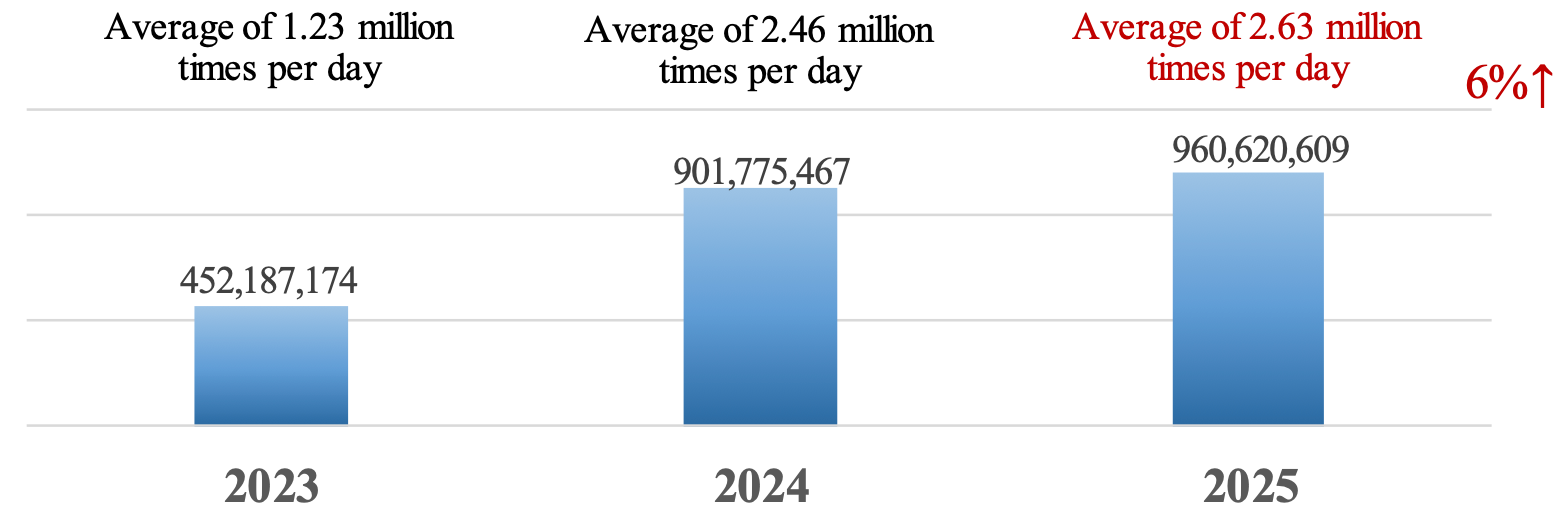
That's the warning from Taiwan’s National Security Bureau (NSB), which has released new figures showing daily cyber intrusions against the island more than doubling from an average of 1.23 million a day in 2023 to 2.63 million attempted breaches in 2025.
Attacks on the energy sector surged by 1,000% over the past year - the largest increase of any industry - while emergency services and hospitals were the second-most targeted, with intrusions up 54%.
The NSB said the escalation in cyberattacks appears to have been deliberately timed to coincide with so-called ‘joint combat readiness patrols" - People's Liberation Army exercises that double as both a show of force and a possible rehearsal for a future invasion.
China is also accused of stepping up hacking during "major ceremonies", overseas trips by senior Taiwanese officials, and even the first anniversary of President Lai’s inauguration to "disrupt government services and undermine public morale".
"China has fully integrated its public and private resources across its military, intelligence, industry, and technology sectors," the NSB wrote in a report published this week.
"Through diverse hacking measures and technologies, China has enhanced penetration and concealment capabilities of its external cyberattacks.
"The NSB urges all nationals to raise their cybersecurity awareness and remain vigilant against cyber threats posed by China, so that we can jointly safeguard the comprehensive cybersecurity of Taiwan."
Chinese cyber-army's digital blitzkrieg
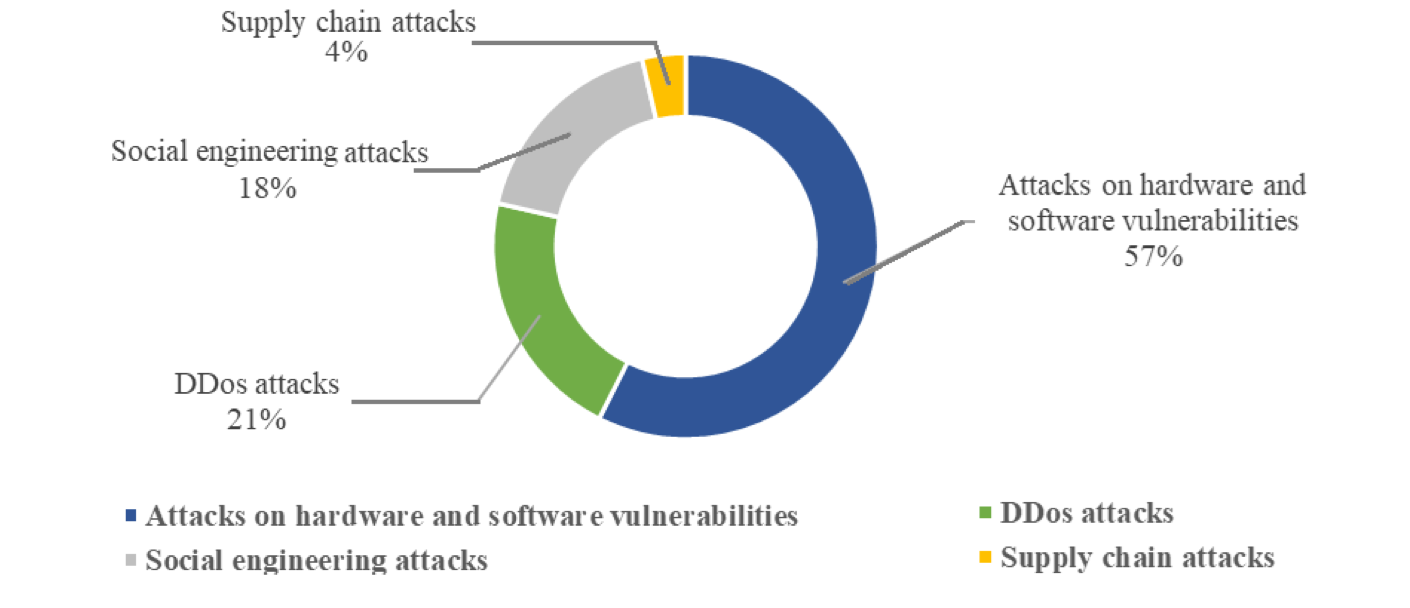
Taiwan’s National Security Bureau said five major Chinese hacking groups -BlackTech, Flax Typhoon, Mustang Panda, APT41 and UNC3886 - launched coordinated cyber operations against the island.
According to the agency, attackers conducted extensive probing of network equipment and industrial control systems at energy companies, implanted malware in corporate systems, and deployed ransomware to disrupt operations at major hospitals.
Data stolen from medical institutions was later offered for sale on dark-web forums. At least 20 such incidents were identified in 2025 alone.
READ MORE: Five Eyes probes LLM-wielding hacker-for-hire in China’s state-controlled digital underworld
The NSB said China’s “cyber army” also exploited weaknesses in Taiwan’s telecommunications networks, hacking service providers and subcontractors in order to infiltrate sensitive and backup communications links.
At the same time, highly targeted social-engineering emails were sent to specific central government agencies in an apparent effort to breach internal systems.
The campaign has extended across the semiconductor and defence supply chain, from upstream manufacturers to downstream contractors and science parks.
Those operations, the NSB warned, were designed to steal advanced technologies, industrial plans and high-level decision-making intelligence.
"'Make a sound in the East, then strike in the West"
Gavin Knapp, Cyber Threat Intelligence Principal Lead at Bridewell, warned that the cyberwar was not likely to abate anytime soon.
"The increase of such attacks on critical infrastructure is likely to continue, particularly given China’s strategic, long-term interest in Taiwan, and it’s also possible that Russia’s activity in Ukraine and the response to it could provide encouragement and help inform China’s future plans regarding Taiwan," he said.
"State-sponsored espionage and prepositioning, which China is known for, continues to operate in a grey area where the consequences largely go unpunished compared with engaging in kinetic warfare operations. It's possible China would also likely encourage state-backed proxy groups to target Taiwan, and incentivise or turn a blind eye to cybercrime activity that targets the region."
"Both CISA and the UK's NCSC issued advisories in the past 18 months, which aligns with China's targeting of critical national infrastructure, so it's likely these sectors would be targeted in Taiwan. Volt Typhoon and Salt Typhoon (Telecoms) are two Chinese threat actors that this targeting aligns with."
READ MORE: Ex-CISA chief: Stop calling Chinese hackers silly names and start taking them seriously
Darrel Lang, Cyber Threat Intelligence Analyst at Bridewell, suggested China may be waging a digital war of attrition (our words, not his) in a bid to wear down its opponent.
"The increase in attack volume could itself be perceived as a tactic to induce alert fatigue and numbness, not only to mask more significant impacts that may or may not “get through,” but also to create a constant state of distraction. This would draw the attention of both Taiwan, as the direct target, and other invested entities concerned about their interests in the region.
"There is a set of Chinese military strategies known as 'The Thirty-Six Strategems', one of which is 'Make a sound in the East, then strike in the West'. This essentially describes the tactic of diverting attention in one direction before taking action elsewhere.
"I’m not suggesting this is necessarily what is happening here, but when it comes to Chinese state-directed activity, the surface picture is rarely the only one worth considering."




