Microsoft blames China for SharePoint ToolShell attacks, governments and nuclear weapons agency targeted
Fear turned to panic as scary 9.8 CVSS vulnerability came under active exploitation by bad guys including nation-state attackers.

Microsoft has alleged that China-linked threat actors are responsible for exploiting a SharePoint vulnerability dubbed ToolShell that has been leveraged to carry out attacks on a Western government and a US nuclear agency.
Exploitation of the "high-severity, high-urgency" zero-day was confirmed last week - depending on who you ask. It's now being tracked as CVE-2025-53770, has a nasty 9.8 CVSS score and enables an unauthorised attacker to execute code over a network via the deserialisation of untrusted data in on-premises Microsoft SharePoint Servers.
In a statement, Redmond said it has observed two named Chinese nation-state actors called Linen Typhoon and Violet Typhoon exploiting these vulnerabilities targeting internet-facing SharePoint servers, as well as another China-based threat actor called Storm-2603 using them deploy ransomware.
It wrote: "Investigations into other actors also using these exploits are still ongoing. With the rapid adoption of these exploits, Microsoft assesses with high confidence that threat actors will continue to integrate them into their attacks against unpatched on-premises SharePoint systems."
Microsoft has rushed out two emergency patches for Toolshell (a variant of CVE-2025-49706 that was supposedly fixed on Patch Tuesday, only to reappear last week and spark global panic). It also issued the following advice to enterprises that were unable to follow its advice to install the patches and then engage Antimalware Scan Interface to stop unauthenticated attackers from exploiting the vulnerability.
"We recommend you consider disconnecting your server from the Internet until you have applied the most current security update," it wrote.
"If the server cannot be disconnected from the internet, consider using a VPN or proxy requiring authentication or an authentication gateway to limit unauthenticated traffic."
Bloomberg later reported that the US National Nuclear Security Administration had been breached, although no sensitive or classified information was stolen.
The NNSA is responsible for securing 5,000 nuclear warheads, monitoring for radiation leaks and ensuring nukes do not accidentally explode, causing devastation across America.
Initial evidence of nation-state threat actors exploiting ToolShell
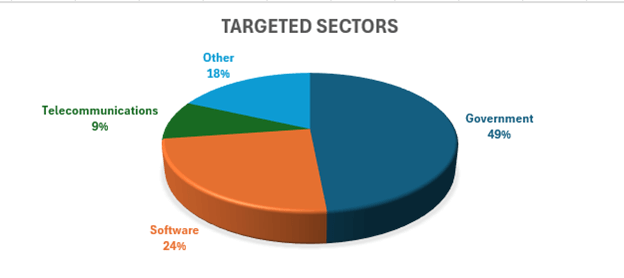
Charles Carmakal, Google's Mandiant CTO, was one of many prominent industry voices to confirm Toolshell had been exploited in the wild by nation-state attackers.
"The early zero-day exploitation was broad and opportunistic," he said. "We're aware of victims in several sectors and global geographies. The activity primarily involved the theft of machine key material which could be used to access victim environments after the patch has been applied.
"We assess that at least one of the actors responsible for the early exploitation is a China-nexus threat actor. Multiple threat actors are actively exploiting this vulnerability now."
READ MORE: Europol leads global takedown of pro-Russian hacktivist group NoName057(16)
Lotem Finkelstein, director of threat intelligence at Check Point Research, backed this assessment and said: "The nature of this campaign - stealthy, highly targeted, and aimed at government and telecom sectors - strongly suggests the work of a nation-state actor and points to a broader espionage effort."
Check Point identified dozens of exploitation attempts stretching all the way back to July 7th - including an attack on a "major Western government".
"This exploitation campaign reinforces the critical need to monitor and defend legacy and on-premise infrastructure," it wrote.
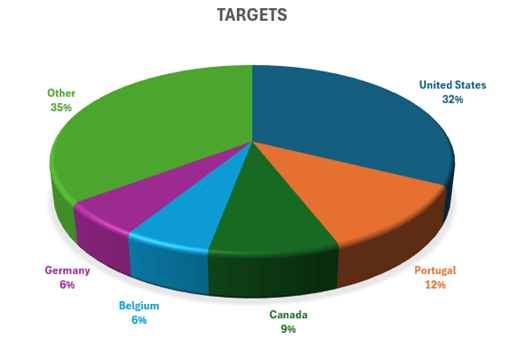
Researchers from Rapid7 also alleged that Toolshell was exploited in the wild as a zero-day by an "unknown threat actor" before Microsoft's disclosure.
"This vulnerability is being used in widespread, aggressive campaigns to achieve RCE, establish persistent access, and extract cryptographic keys that allow attackers to forge valid authentication tokens," it warned.
"This campaign is not opportunistic - it is deliberate, capable, and designed for persistence even after patching. Rapid7 has observed active exploitation in customer environments and is sharing indicators of compromise, and detection guidance to help defenders respond quickly.
Meanwhile, SentinelOne identified three "distinct attack clusters" with "unique tradecraft and objectives".
READ MORE: Cascading risk: Protecting against supply chain attacks in a hostile threat landscape
It wrote: "We have observed initial ToolShell exploitation against high-value organisations, with victims primarily in technology consulting, manufacturing, critical infrastructure, and professional services tied to sensitive architecture and engineering organisations. The early targets suggest that the activity was initially carefully selective, aimed at organisations with strategic value or elevated access.
"Activity following the public disclosure is opportunistic and likely unrelated to the original we describe here. We expect broader exploitation attempts to accelerate, driven by both state-linked and financially motivated actors seeking to capitalize on unpatched systems.
"SentinelOne has observed multiple state-aligned threat actors, unrelated to the first wave of exploitation, beginning to engage in reconnaissance and early-stage exploitation activities.
"Additionally, we’ve also identified actors possibly standing up decoy honeypot environments to collect and test exploit implementations , as well as sharing tooling and tradecraft across known sharing platforms. As awareness spreads within these communities, we expect further weaponisation and sustained targeting of vulnerable SharePoint infrastructure."
Which security firm first observed Toolshell?
Eye Security claimed to be the first to identify large-scale exploitation of the SharePoint bug, which it first observed on July 18th. Three days earlier, an offensive security team from Code White GmbH demonstrated an unauthenticated RCE exploit chain in SharePoint using a combination of two bugs presented at Pwn2Own Berlin in May 2025 (CVE-2025-49706 & CVE-2025-49704).
However, other researchers are stepping up to say they knew about the bug was being targeted days or even weeks beforehand.
As mentioned earlier, Check Point Research stated that it identified the first signs of exploitation on July 7th, while SentinelOne reported that saw bug being attacked on July 17th, prior to Microsoft's official advisories.
Eye Security found the active exploitation by scanning more than 8000 SharePoint servers worldwide, identifying dozens of systems compromised during four confirmed waves of attack.
READ MORE: ChatGPT Agent excels at finding ways to "cause most harm with least effort", OpenAI reveals
An alert from one of its CrowdStrike Falcon EDR deployments flagged a suspicious process chain on a legacy SharePoint on-prem server linked to a recently uploaded malicious .aspx file.
Eye Security wrote: "At first glance, it looked familiar. A classic web shell, obfuscated code in a custom path, designed to allow remote command execution via HTTP. We’ve seen many of these before. What made this one stand out, however, was how it got there."
It later found a "stealthy spinstall0.aspx file" designed to extract and leak cryptographic secrets from SharePoint server using a GET request.
This wasn’t a "typical webshell" and had no interactive commands, reverse shells, or command-and-control logic, instead invoking internal .NET methods to read the SharePoint server’s MachineKey configuration, including the ValidationKey.
"These keys are essential for generating valid __VIEWSTATE payloads, and gaining access to them effectively turns any authenticated SharePoint request into a remote code execution opportunity," Eye Security explained.
"The new ToolShell CVE chain likely completes full Remote Code Execution (RCE): utilising the way SharePoint handles deserialization and control rendering via __VIEWSTATE," it added.
"These payloads can embed any malicious commands and are accepted by the server as trusted input, completing the RCE chain without requiring credentials. This mirrors a design weakness exploited in 2021, but now packaged into a modern zero-day chain with automatic shell drop, full persistence, and zero authentication."
Stealing secrets: Cryptographic thievery
Robert Hann, Global VP Technical Solutions at Entrust, described cryptographic asset theft as "the new phishing".
"Bad actors have learnt that, like stealing passwords, getting an important cryptographic asset like API Keys or a Machine Identity, is much easier than brute force methods," he said. "Once stolen, the power of these credentials means they get broad and often deep access to the most sensitive data and systems in one or many organisations.
“This is why enterprises must embrace a Zero Trust mindset, and assume that breaches will occur. Continuously assessing cryptographic asset risks to find vulnerabilities by way of automated compliance profiling provides actionable insights that are critical to minimising damage and preventing a breach in the first place.
"To protect sensitive data with encryption and HSMs, it’s essential to first understand which cryptographic assets—like private keys, digital certificates, and encryption algorithms—are securing which systems and information. Leveraging an HSM is especially important for data that is sensitive or carries compliance requirements.
"In addition to HSM protection, it's crucial for companies to implement other security best practices for SharePoint, such as keeping the software up to date with the latest patches and security updates, using strong passwords, rolling over keys regularly and following secure configuration guidelines."




