Chinese threat actors use Google Calendar to attack US government targets
The notorious APT41 group snuck a malware payload onto official websites and hid stolen data inside Calendar events.

Chinese hackers have been caught using Google Calendar to attack the US government.
Google Threat Intelligence Group has discovered that a Chinese threat actor called APT41 (or HOODOO to its enemies) cracked into a government website, boobytrapped it and then targeted "multiple other government entities", which have not been identified.
The exploited site was jerry-rigged to deliver malware Google has named “TOUGHPROGRESS”.
This payload "took advantage of Google Calendar" for command and control (C2), a technique that enables the bad guys to sneak into cloud services by blending their malicious actions with legitimate activity to avoid detection.
"We assess with high confidence that this malware is being used by the PRC (People's Republic of China) based actor APT41," Google wrote.
"APT41’s targets span the globe, including governments and organisations within the global shipping and logistics, media and entertainment, technology, and automotive sectors."
A date with destiny
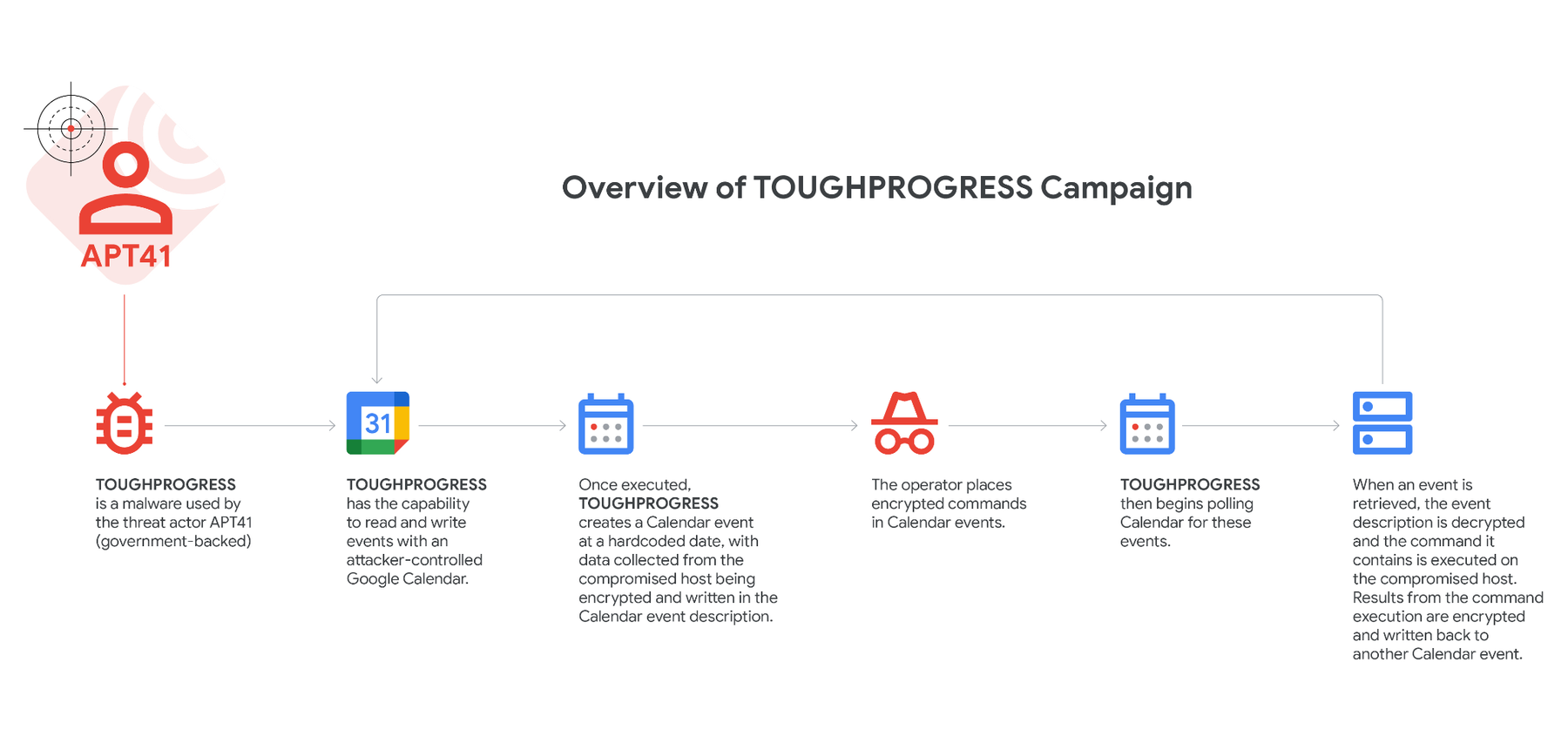
TOUGHPROGRESS can read and write events on an attacker-controlled Google Calendar.
APT41 sent spear-phishing emails containing a link to a ZIP archive stored on the compromised government website. This archive contains an LNK file "masquerading as a PDF" and a directory containing seven JPG images of arthropods.
"When the payload is executed via the LNK, the LNK is deleted and replaced with a decoy PDF file that is displayed to the user indicating these species need to be declared for export," Google wrote.
"This malware has three distinct modules, deployed in series, each with a distinct function," it added. "Each module also implements stealth and evasion techniques, including memory-only payloads, encryption, compression, process hollowing, control flow obfuscation, and leveraging Google Calendar for C2."
These modules are:
PLUSDROP - A Dynamic Link Library (DLL) to decrypt and execute the next stage in memory.
PLUSINJECT - This launches and performs process hollowing, which removes code in an executable file and replaces it with malicious code. In this case, PLUSINJECT targeted a legitimate “svchost.exe” process, pumping it with a final payload.
TOUGHPROGRESS - Executes actions on the compromised Windows host and deploys Google Calendar for C2 command and control.
A payload's progress

Once executed, TOUGHPROGRESS creates a zero-minute Calendar event at a hardcoded date (May 30th 2023). Data is then collected from the compromised host before being encrypted and secretly stored in the Calendar event description. Interestingly and probably coincidentally, Ukraine launched a series of drone attacks against Moscow on this exact date.
Princess Eugenie also gave birth to her son, Ernest George Ronnie, on the same day. But that's even less likely to be relevant.
The malware operator put encrypted commands inside Calendar events on July 30th and 31st 2025 - which are also dates hardcoded into the malware.
TOUGHPROGRESS polls Calendar for these events. When one is retrieved, the event description is decrypted and the command it hides is then executed on the compromised host machine.
Subsequently, the results of the command execution are encrypted and hidden in another calendar event.
Making TOUGHPROGRESS
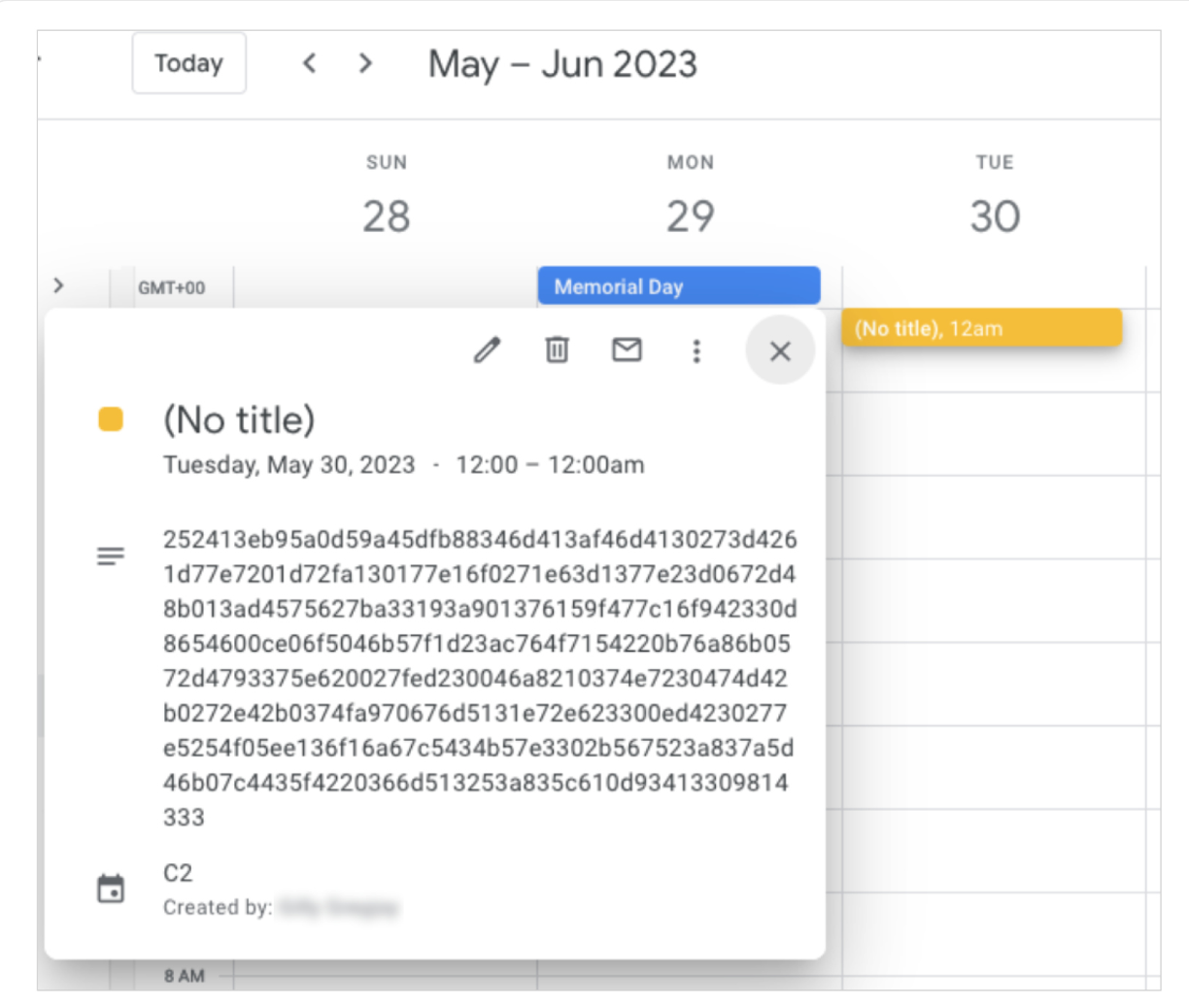
Google reverse engineered the C2 encryption protocol used in TOUGHPROGRESS, to find a 10-byte XOR key that generates a per-message 4-byte XOR key.
It was first compressed with LZNT1 and encrypted it using XOR with a 4-byte (32-bit) key.
A 10-byte header was then created to store metadata. This header was encrypted with the 10-byte XOR key, added to the header of a message. The combined encrypted header and message is then hidden in the Calendar event description, wherein the badness lies.
The Google Threat Intelligence Group has been "actively monitoring and protecting against APT41’s attacks using Workspace apps for several years".
"This threat group is known for their creative malware campaigns, sometimes leveraging Workspace apps," it warned.
Advanced, persistent, threatening
APT 41 lives up to its acronym and is certainly a persistent threat that uses advanced and innovative tactics.
In October 2024, Proofpoint attributed the VOLDEMORT malware campaign to APT41.
And in 2019 and 2020, the FBI indicted five Chinese nationals from APT41 and BARIUM for global cyberattacks, supply chain intrusions, and ransomware operations targeting tech, telecom, and government sectors.
For more information and full TPPs, read Google's full blog.
Do you have a story or insights to share? Get in touch and let us know.




