Dark web Initial Access Brokers are selling hacked network access for as little as $500, study reveals
Investigators find that crooks offer consumer-style hack'n'mix bundles that package access with privilege or other treats.

Initial Access Brokers lurk on dark web forums and marketplaces, selling an illegal product that's in hot demand.
These increasingly prominent cybercrime players do the hard work of cracking into systems - then flog the access they've gained to the highest bidder.
Today, they're becoming increasingly professional, offering hack'n'mix deals which combine network access bundled with other goodies.
Researchers from the security firm Rapid7 found that IABs are offering consumer-style bundles that give multiple routes into a business, several forms of privilege, or a mixture of both.
Brokers offer a "diversity of options" to would-be attackers, with a business model founded on the sad fact that initial access to victims' networks is both "inexpensive and easy to obtain", Rapid7 wrote in its report.
"All the willing buyer has to do is pay a few hundred dollars to gain immediate access to an already compromised business," the researchers warned.
"In the end, they’ve gotten into your business for as little as $500 and your business has lost upwards of $5 million (or more)."
Buying the services of IABs lets low-skilled hackers penetrate organisations that would be unattainable under normal circumstances. Additionally, IABs also serve professional, potentially even nation-state-linked customers who want to save time on mapping out initial access vectors.
Dodgy deals on the dark web
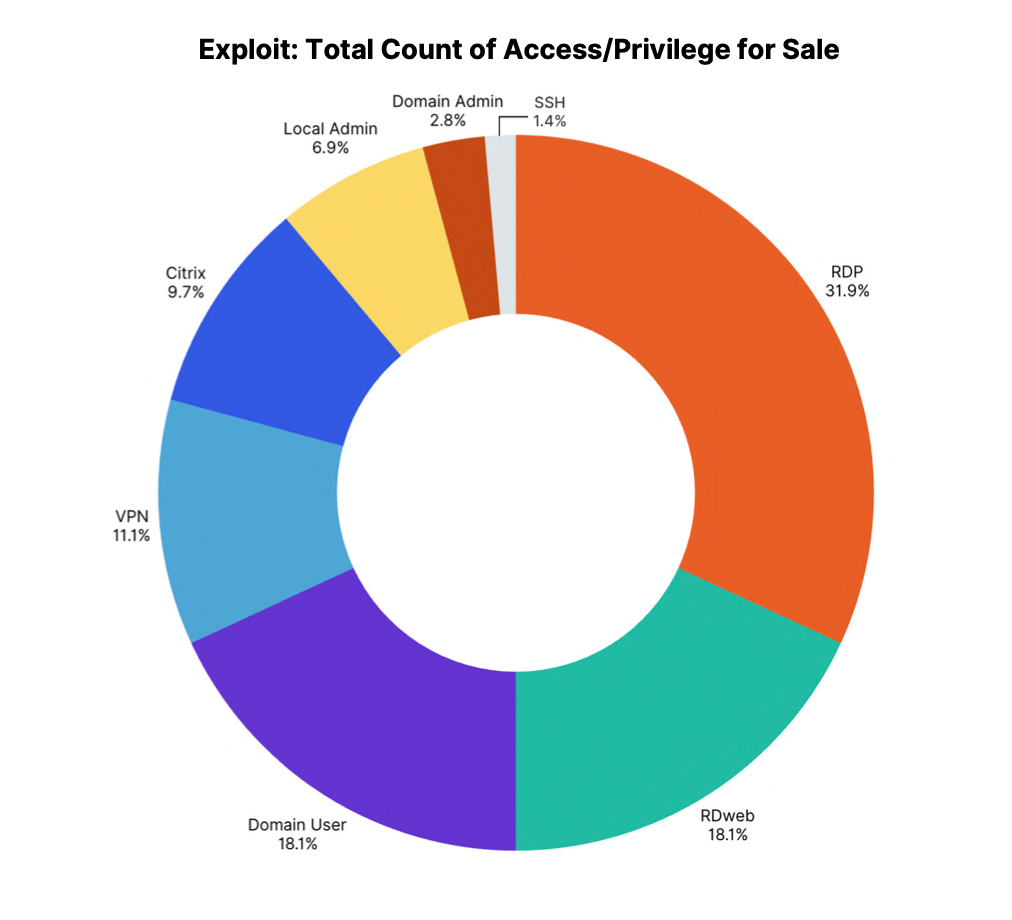
The 2025 Access Brokers Report draws on six months of threat intelligence from the infamous dark web forums Exploit, XSS and BreachForums.
Like all good service providers, access brokers underpromise and overdeliver, because the word "initial" doesn’t quite reflect their true level of access, which often involves a "deep compromise".
Raj Samani, SVP and chief scientist at Rapid7, said: "This report shows that initial access brokers aren’t intent upon finding a single way into an organisation’s network and then quickly exiting — they’re making attempts to explore the networks they’ve infiltrated. And they’re often succeeding.
"In doing so, the IAB can offer buyers admin privileges, multiple access types, or both. By the time a threat actor logs in using the access and privileged credentials bought from a broker, a lot of the heavy lifting has already been done for them.
"Therefore, it’s not about if you’re exposed, but whether you can respond before the intrusion escalates."
READ MORE: The rise of Dark LLMs: DDoS-for-hire cybercriminals are using AI assistants to mastermind attacks
The report found:
- The vast majority of access broker sales (71.4%) offer more than just a specific access vector; they also include a level of privilege, and in nearly 10% of those sales, it’s a bundle with multiple initial access vectors and/or privileges.
- The average sale price hovered just over $2,700, with nearly 40% of offerings priced between $500–$1,000.
- VPN, Domain User, and RDP were the most common access types — the very same weak points seen in Rapid7’s incident response investigations.
Rapid7 said its report is published against a backdrop of continued struggles against "alert fatigue, limited resources, and evolving attacker tradecraft" - the familiar and perhaps eternal foes of all cybersecurity professionals.
READ MORE: Meet "Mommy": An East Asian Dark Web Initial Access Broker
It advised organisations to:
- Enforce MFA — especially on VPN, RDP, and user accounts that access critical infrastructure.
- Invest in threat-informed detection and response — including unified platforms that correlate access signals with suspicious activity.
- Run regular red team exercises to identify exposure paths like abandoned accounts, default credentials, and externally accessible RDP services.
Making a deal:
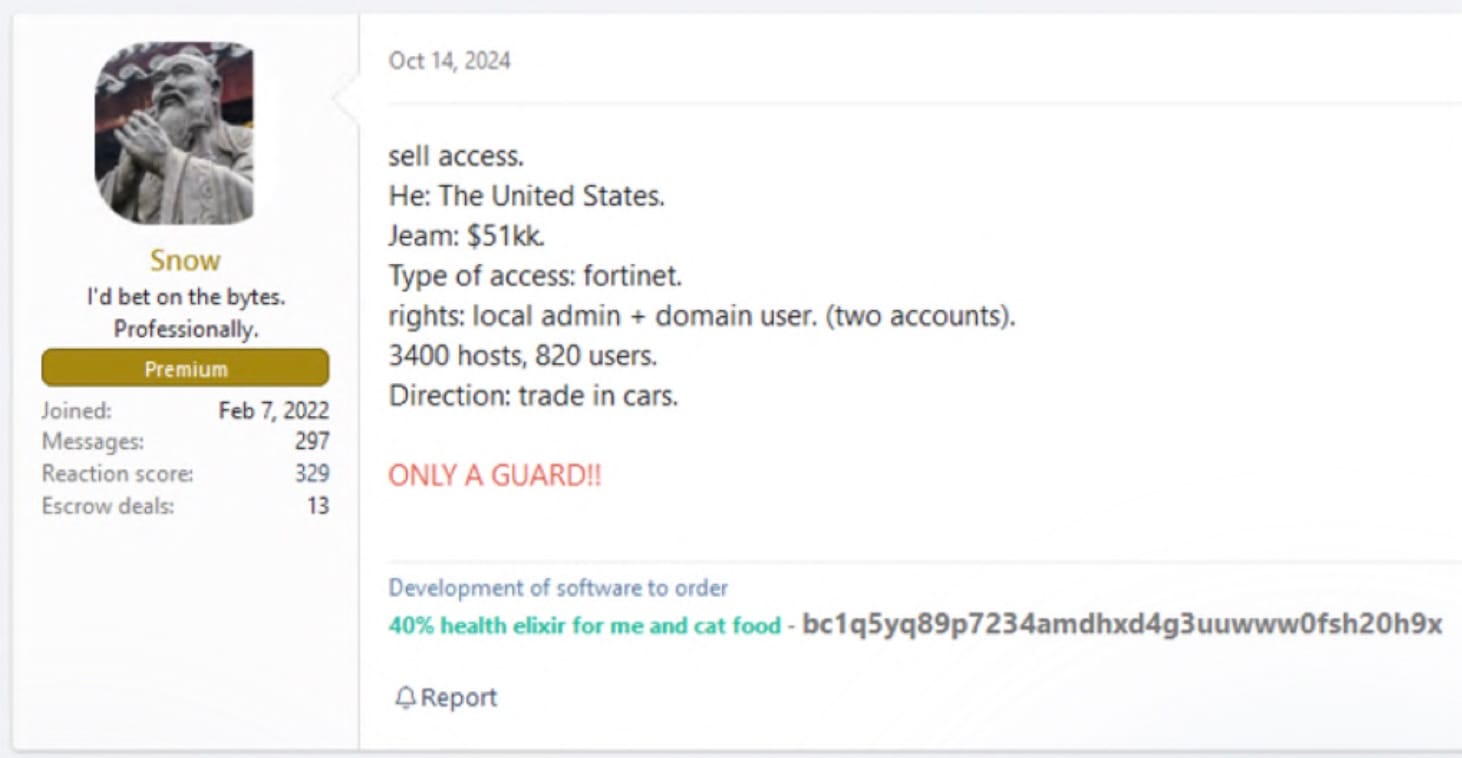
The average base sale price for a dark web bundle is $2,726, and the average indicated annual revenue of the victim organisation is "in the region of $2.232 billion", Rapid7 reported.
Broker sales in its data broadly fell into one of three types:
- Regular: A single IAV which permits access to a compromised business (28.6% of the posts Rapid7 examined). This could be a standalone VPN sale, or standalone RDP access only. There's no privilege included.
- Large: An IAV with one form of privilege included (62.6%). Brokers can "sweeten the deal" by including a specific form of privilege, which allows for faster traversal of an environment. An example could be selling RDP with domain user credentials plus a combo of a VPN and admin account.
- Supersized: Bundle deals where the sale includes a combination of IAVs and/or privilege types (8.8%). The seller may be offering multiple routes into a business, several forms of privilege, or a mixture of both. The main aspect of these bundles is that the broker is selling three or more compromised aspects of a business
"The best-case scenario for a compromised business is that the broker 'only' has one form of IAV for sale," Rapid7 warned.
"In the worst-case scenario, a broker potentially gains significant progress to the victim’s network, and takes at least one form of potential privilege under their wing.
"In this case, victims are in serious trouble long before a payment has been made, and that’s without considering how long the broker may have lived on the network without detection.
READ MORE: Have cops seized Abacus Market? Rumours swirl as dark web drugs bazaar shuts down
"Make no mistake, a business in this predicament is essentially being compromised twice over, by broker and buyer, and at no point has their security solution been able to detect either form of illicit access.
"All of this, before stopping to consider what, exactly, the broker has stolen for themselves on their way out the door — assuming they ever left.
"If your business is compromised by an access broker, you’re in bad shape. But if your business has somehow ended up in that worst-case scenario, threat actors have essentially declared open season."




