Europol leads global takedown of pro-Russian hacktivist group NoName057(16)
Cops smash Moscow-linked group blamed for a number of DDoS attacks and believed to wield a huge botnet.

Europol has launched an international sting against a pro-Russian cybercrime network called NoName057(16).
Cops in a dozen countries around the world simultaneously swooped on suspects and infrastructure linked to the shadowy hacktivists, who have been linked to a number of incidents.
In 2023 and 2024, the criminal network is alleged to have taken part in attacks against Swedish authorities and bank websites. Since investigations started in November 2023, Germany has also experienced 14 waves of attacks targeting more than 250 companies and institutions.
Switzerland suffered multiple attacks in June 2023 as Ukrainian officials delivered a video message to the Joint Parliament, and also in June 2024 during the Peace Summit for Ukraine at Bürgenstock.
The Dutch authorities recently confirmed that an attack linked to this network was carried out during the latest NATO summit in the Netherlands.
"These attacks have all been mitigated without any substantial interruptions," Europol claimed.
Do you feel lucky, punk?
Authorities in Czechia, France, Finland, Germany, Italy, Lithuania, Poland, Spain, Sweden, Switzerland, the Netherlands and the United States took part in a joint international operation called Eastwood on 14 and 17 July (hence the Clint Eastwood video shared above).
These actions led to the disruption of an attack infrastructure made up of more than one hundred computer systems worldwide, leading to a "major part of the group's central server infrastructure" being taken offline.
Germany also issued six arrest warrants for offenders living in the Russian Federation, who we're sure are probably not quaking in their boots at the thought of German cops being ineffectively miffed on the other side of the rebuilt Iron Curtain.
Two of these persons are accused of being the "main instigators responsible for the activities of NoName057(16)".
In total, national authorities have now issued seven arrest warrants against six Russian nationals for their involvement in the gang's activities. All of the suspects are listed as internationally wanted and five profiles were also published on the EU Most Wanted website.
Additionally, law enforcement has reached out to several hundred individuals who are believed to be supporters of the cybercrime network.
"The messages, shared via a popular messaging application, inform the recipient of the official measures highlighting the criminal liability they bear for their actions pursuant to national legislations," Europol wrote.
"Individuals acting for NoName057(16) are mainly Russian-speaking sympathisers who use automated tools to carry out distributed denial-of-service (DDoS) attacks. Operating without formal leadership or sophisticated technical skills, they are motivated by ideology and rewards."
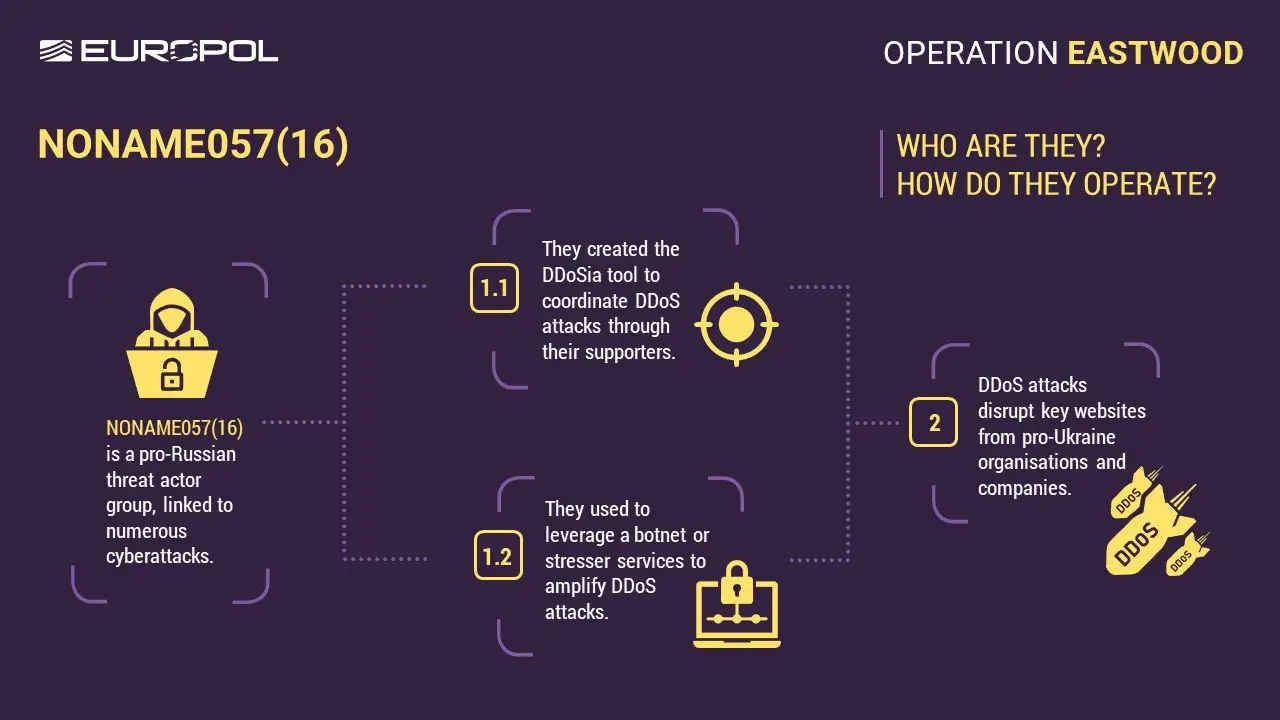
The operation resulted in:
- 2 arrests (1 preliminary arrest in France and 1 in Spain)
- 7 arrest warrants issued (6 by Germany, and 1 by Spain)
- 13 individuals questioned (2 in Germany, 1 in France, 4 in Italy, 1 in Poland, 5 in Spain)
- Over 1,000 supporters, including 15 administrators, were told of their potential legal liability via a messaging app (which we're presuming is Telegram).
- Over 100 servers disrupted worldwide
- Major part of NoName057(16) main infrastructure taken offline
24 house searches (2 in Czechia, 1 in France, 3 in Germany, 5 in Italy, 12 in Spain, 1 in Poland)
Investigating NoName057(16)

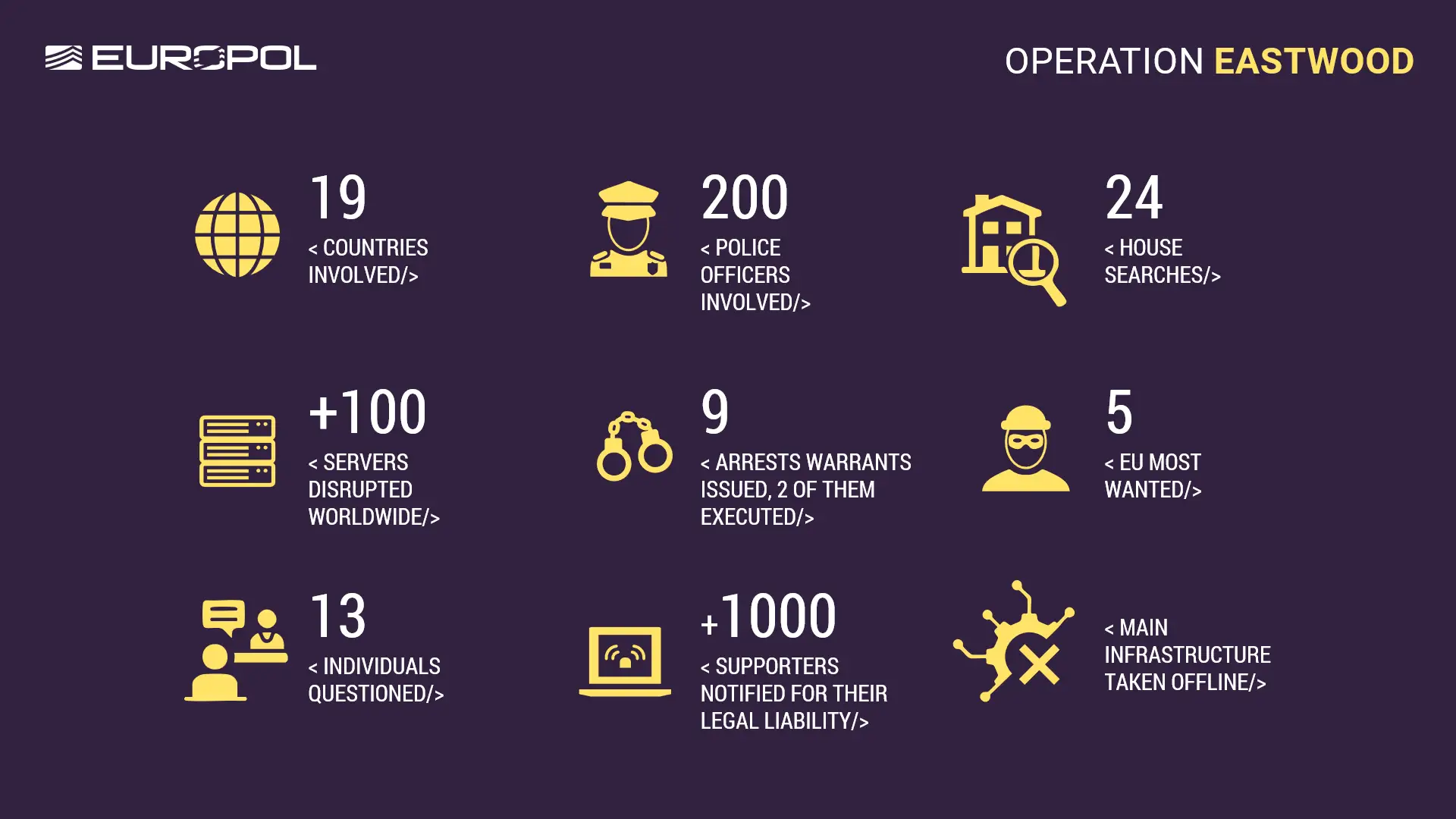
This rather clumsily named group is believed to be an "ideological criminal network" that supports Russia and has been blamed for a number of DDoS attacks linked to the war in Ukraine.
It is believed to have a 4,000-strong network of supporters and wield a bonnet comprising several hundred servers.
Explaining its tactics, Europol wrote: "To share calls to action, tutorials, updates, and to recruit volunteers, the group leveraged pro-Russian channels, forums, and even niche chat groups on social media and messaging apps.
"Volunteers often invited friends or contacts from gaming or hacking forums, forming small recruitment circles. These actors used platforms like DDoSia to simplify technical processes and provide guidelines, enabling new recruits to become operational quickly.
"Participants were also paid in cryptocurrency, which incentivised sustained involvement and attracted opportunists.
"Mimicking game-like dynamics, regular shout-outs, leader boards, or badges provided volunteers with a sense of status. This gamified manipulation, often targeted at younger offenders, was emotionally reinforced by a narrative of defending Russia or avenging political events."
Unfortunately, Operation Eastwood is unlikely to have totally wiped out the pro-Russian crime gang, warned Rafa López, security engineer at Check Point, who said: "While the recent international crackdown on the NoName057(16) group has disrupted their operations, it is unlikely to mark the end of their activities. This Russia-affiliated hacktivist group, which primarily targets countries with anti-Russian stances, continues to operate through encrypted channels like Telegram and Discord.
"Although their DDoS capabilities have been reduced, they are shifting toward more sophisticated methods, including system intrusions and data exfiltration. The group remains active and has built a vast network of affiliates, with thousands of volunteers across various platforms, including online gaming and hacktivist forums.
"As experts in cybersecurity, we recommend that organisations strengthen their defences by implementing multi-layered security strategies, including robust DDoS protection, intrusion detection systems, and regular security audits. It is also essential to educate employees about the risks of cyberattacks, as well as to monitor for unusual activities on communication platforms that might indicate potential recruitment efforts. By staying vigilant and proactive, companies can better safeguard themselves against evolving threats from groups like NoName057(16)."




