Fake Kling AI ads are stealing Facebook users' personal data
"From deepfake scams to impersonation attacks, the rising trust in AI-powered platforms has created new openings for cyber criminals."

KlingAI is a powerful generative video app known for producing uncannily realistic footage based on a text or image.
So there is a certain irony in the news that fake Kling AI Facebook adverts are being used to steal victims' sensitive data.
Check Point Research has warned that threat actors are "exploiting the AI boom" and "targeting trust in generative platforms" to fool people into downloading malicious files which harvest their valuable information.
In early 2025, it identified a cyber attack campaign that "exploited the popularity" of Kling AI, which has roughly six million users worldwide.
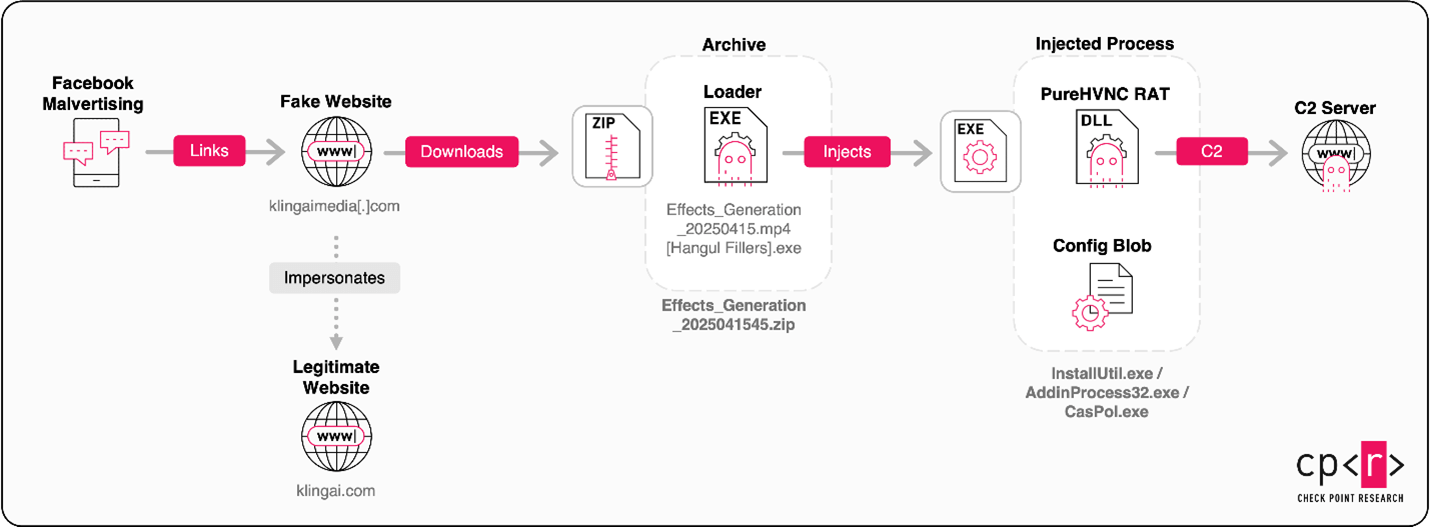
The campaign used deceptive social media ads to draw people into visiting a fake website a fake website which executed a remote access trojan (RAT), enabling attackers to seize control of the victim’s system and steal anything they can get their hands on.
"The malware deployed in this campaign featured advanced evasion techniques, including file masquerading to disguise harmful executable files as harmless media files, and extensive anti-analysis methods to avoid detection," Check Point wrote.
"As generative AI continues to capture global attention, threat actors are quick to exploit AI’s capabilities and popularity. From deepfake scams to impersonation attacks, the rising trust in AI-powered platforms has created new openings for cyber criminals."
Kling on to your personal data

Researchers identified roughly 70 fake sponsored posts that closely mimic Kling AI.
"These ads come from convincing but fraudulent Facebook pages designed to look like the real company," Check Point warned.
Clicking on one of these ads leads users to a fake website that also resembles Kling's real interface.
Just like the real Kling, users are invited to upload images and click "generate" to create a video. But if they dare to click on this boobytrapped button, they will download an archive file with a malicious payload.
Although this file looks harmless with a sensible-sounding name like "Generated_Image_2025.jpg" and a familiar image icon, it's actually designed to compromise the user's system.
This technique is known as filename masquerading and is a common tactic used to trick users into launching malicious software.
When opened, the program embeds itself deep within the target system and ensures it will reload itself automatically every time the computer is switched on. The sneaky malware even checks to see if it is being monitored or analysed by cybersecurity tools, and tries to avoid detection.
Silent takeover: Unleashing a dirty RAT
Once a beachhead is established, the RAT is unleashed, allowing attackers to take control of the victim’s computer from a distance.
"Each version of this tool is slightly altered to avoid detection, but all include a hidden configuration file that connects back to the attackers’ server," Check Point wrote. "These files also contain campaign names like “Kling AI 25/03/2025” or “Kling AI Test Startup,” suggesting ongoing testing and updates by the threat actors."
Once its found a rathole in the system, the malware starts monitoring applications such as web browsers and extensions that store passwords or other sensitive data - providing opportunities to steal personal information and maintain long-term persistence.
Who's behind the fake Kling campaign?
Check Point said the evidence "strongly suggests links to Vietnamese threat actors" - although the attacks cannot be attributed with 100% certainty.
"Facebook-based scams and malware campaigns are a known tactic among groups from the region - especially those focused on stealing personal data," it wrote.
"In this case, our analysis revealed multiple clues pointing in that direction. Similar campaigns themed around AI tools have previously contained Vietnamese-language terms within the malware code.
"Consistent with that pattern, we found several references - such as debug messages—in Vietnamese in this latest campaign as well.
These findings align with broader trends observed by other security researchers investigating similar Facebook malvertising efforts."
For legal reasons - and in case it's not totally obvious - we'd like to remind readers that this attack has absolutely nothing to do with Kling AI, which bears zero responsibility for the campaign and is not linked to it in any way.
Do you have a story or insights to share? Get in touch and let us know.




