Sharepoint under attack: Microsoft rocked by "high-severity, high-urgency" Toolshell zero-day
"You should assume that you have been compromised at this point. Patching alone is insufficient to fully evict the threat."

Microsoft has rushed out an emergency fix for a zero-day vulnerability that could give attackers a backdoor into SharePoint and let them grab security keys.
The story began in May when researchers at the Berlin Pwn2Own hacking contest first exploited a bug dubbed Toolshell, allowing them to achieve remote code execution (RCE) in Microsoft SharePoint.
Although Microsoft addressed these flaws in its July Patch Tuesday updates, threat actors later uncovered two new zero-day vulnerabilities that successfully bypassed those patches.
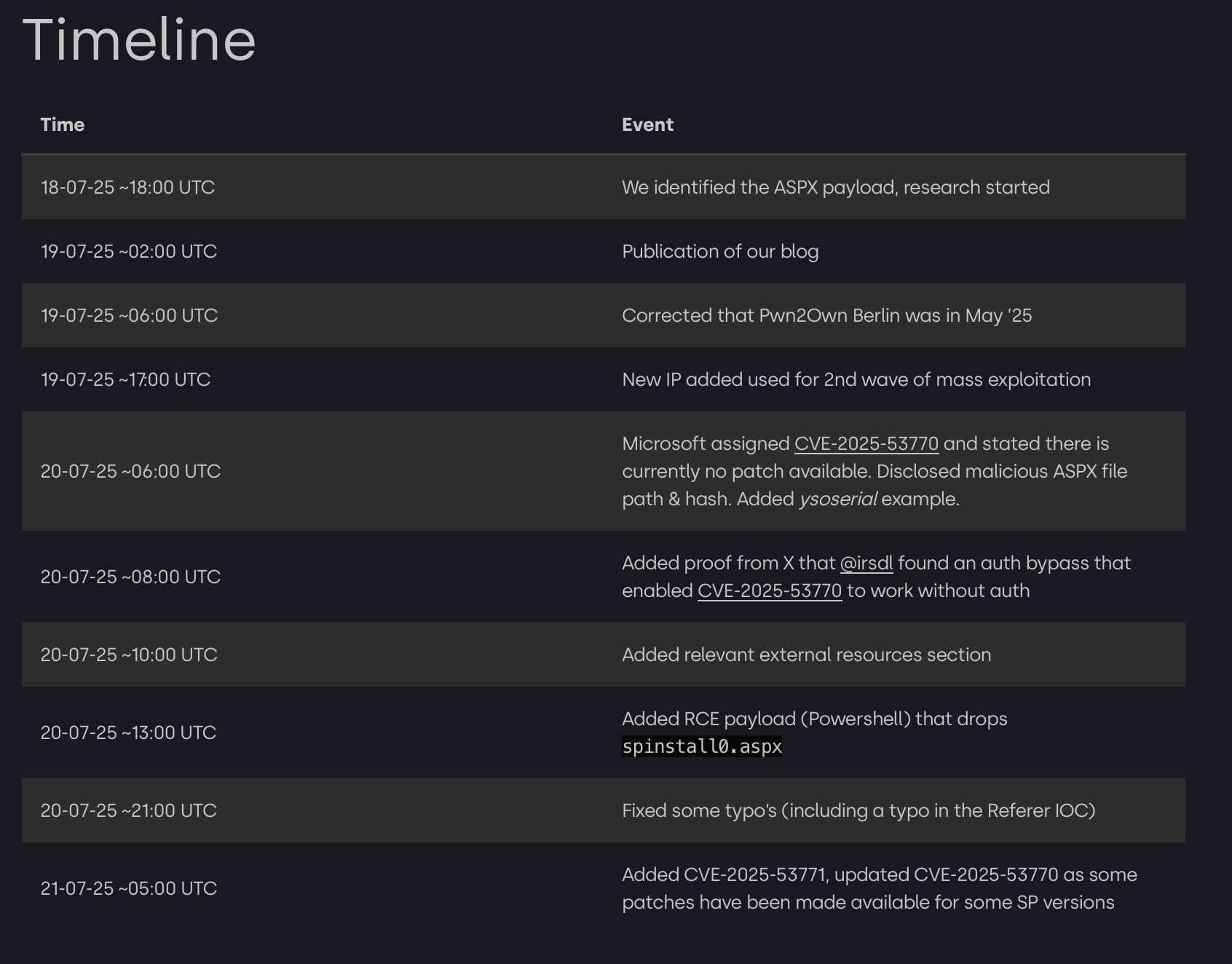
Panic then erupted on the evening of July 18, 2025, when Eye Security announced that it had identified "large-scale exploitation of a new SharePoint RCE vulnerability chain in the wild."
"Demonstrated just days ago on X, this exploit is being used to compromise on-premise SharePoint Servers across the world," it warned.
"Before this vulnerability was widely known last Friday, our team scanned 8000+ SharePoint servers worldwide. We discovered dozens of systems actively compromised during two waves of attack, on 18th of July around 18:00 UTC and 19th of July around 07:30 UTC."
CISA later wrote: "Exploitation activity, publicly reported as 'ToolShell', provides unauthenticated access to systems and enables malicious actors to fully access SharePoint content, including file systems and internal configurations, and execute code over the network."
Governments and corporations compromised
Eye Security said that breached organisations included several multinational corporations and national government entities, such as a private university and an energy sector operator based in California, a federal government health agency, a private AI technology firm, a fintech in New York and a state government organisation in Florida.
It first noticed the attacks after receiving a Falcon EDR alert from a client’s legacy on-prem SharePoint server, observing a suspicious process chain tied to an obfuscated .aspx web shell.
At first, it looked like a typical credential-stuffing attack. But "something didn’t add up".
"That’s when we realised: credentials were never used," Eye Security wrote. "Something deeper—likely a zero-day—was at play."
READ MORE: Cascading risk: Protecting against supply chain attacks in a hostile threat landscape
Microsoft then confirmed it was "aware of active attacks targeting on-premises SharePoint Server customers by exploiting vulnerabilities partially addressed by the July Security Update."
The flaws are being tracked as CVE-2025-53770 and CVE-2025-53771. Redmond said the bugs "could allow arbitrary code to run when a maliciously modified file is opened."
It released emergency patches for the vulnerability with Security Updates for Microsoft SharePoint Server 2019 Core (KB5002754) and SharePoint Server Subscription Edition (KB5002768).
Ghost in the Toolshell
However, the nightmare is not necessarily over for organisations targeted in the zero-day attack wave. If threat actors have stolen their keys, they could return at any point to finish the job - no matter whether the systems have been patched. Which means it's time to cycle those secrets (which you can learn how to do on the Microsoft website).
Eye Security added: "The risk is not theoretical. Attackers can execute code remotely, bypassing identity protections such as MFA or SSO. Once inside, they can access all SharePoint content, system files, and configurations and move laterally across the Windows Domain.
"More concerning is the theft of cryptographic keys. These keys allow attackers to impersonate users or services, even after the server is patched. So patching alone does not solve the issue, you need to rotate the cryptographic material allowing all future IIS tokens that can be created by the malicious actor become invalid.
"Attackers can maintain persistence through backdoors or modified components that survive reboots and updates. So please consult expert incident response services if in doubt."
Which organisations are at risk from Toolshell variant?
Michael Sikorski, CTO and Head of Threat Intelligence for Unit 42 at Palo Alto Networks, said that cloud environments remain unaffected, but on-prem SharePoint deployments - particularly within government, schools, healthcare including hospitals and large enterprise companies - are "at immediate risk"
He said: "Attackers are bypassing identity controls, including MFA and SSO, to gain privileged access. Once inside, they’re exfiltrating sensitive data, deploying persistent backdoors, and stealing cryptographic keys. The attackers have leveraged this vulnerability to get into systems and are already establishing their foothold. If you have SharePoint on-prem exposed to the internet, you should assume that you have been compromised at this point. Patching alone is insufficient to fully evict the threat.
READ MORE: Europol leads global takedown of pro-Russian hacktivist group NoName057(16)
"What makes this especially concerning is SharePoint’s deep integration with Microsoft’s platform, including their services like Office, Teams, OneDrive and Outlook, which has all the information valuable to an attacker. A compromise doesn’t stay contained—it opens the door to the entire network.
"This is a high-severity, high-urgency threat. We are urging organisations who are running on-prem SharePoint to take action immediately and apply all relevant patches now and as they become available, rotate all cryptographic material, and engage professional incident response.
"An immediate, band-aid fix would be to unplug your Microsoft SharePoint from the internet until a patch is available. A false sense of security could result in prolonged exposure and widespread compromise."




