State-sponsored threat actors launch Clickfix social engineering blitz
Iran, Russia and North Korea deploy new tactic during their "business-as-usual espionage campaigns".

The cybercrime underground is not short of new ideas, giving threat actors from rogue nations access to a large and constantly replenished arsenal of exploits, malware and other digital nasties.
Now Proofpoint has issued a new warning about tactics, techniques, and procedures (TTPs) adopted by shady groups from Iran, Russia and North Korea.
"A major trend in the threat landscape is the fluidity of TTPs," it warned. "Threat actors share, copy, steal, adopt, and test TTPs from publicly exposed tradecraft or interaction with other threat groups.
"Specifically, state-sponsored actors have often leveraged techniques first developed and deployed by cybercriminal actors. For example, North Korean threat actors copying techniques from cybercrime to steal cryptocurrency on behalf of the government, or Chinese groups mimicking cybercrime infection chains to deliver malware in espionage operations."
The latest tool seen in the hands of state-backed hackers is ClickFix, which uses dialogue boxes booby-trapped with instructions to copy, paste, and run malicious commands on victims' machines.
This "creative technique" uses fake error messages, as well as "authoritative" false alarms and instructions which appear to have been generated by the users' operating system.
ClickFix was first seen in March 2024. Soon after, it "flooded the threat landscape."
After ClickFix was road-tested by cyber criminals, it has now found its way into the grasp of "at least four state-sponsored threat actors", Proofpoint reported, who have experimented with it as "part of their business-as-usual espionage campaigns".
Between October 2024 and January 2025, threat actors originating from the three previously identified countries incorporated ClickFix in their infection chains.
Kim'll Clickfix it: North Korea in the spotlight
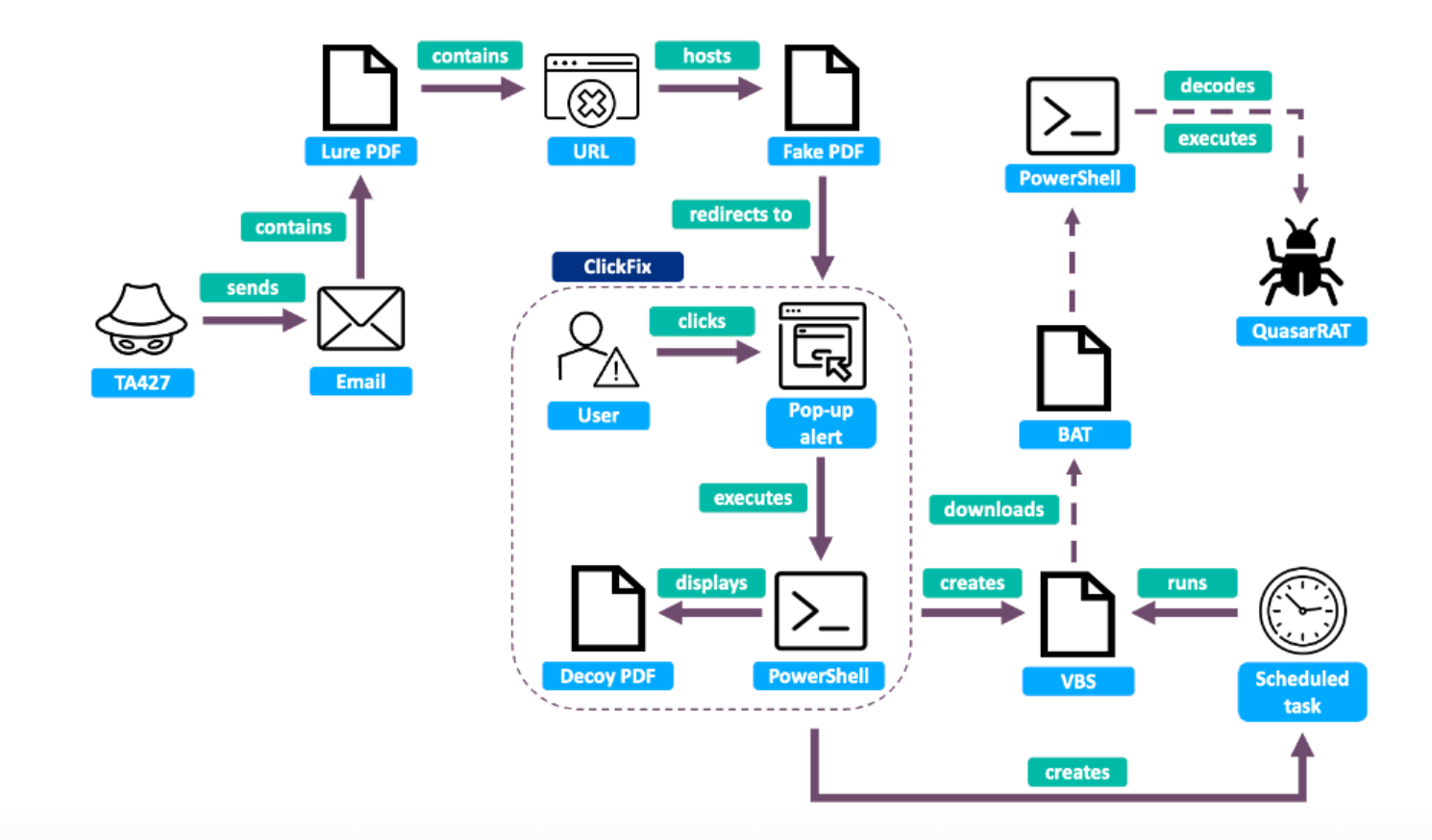
Between January and February 2025, Proofpoint observed a gang called TA427, believed to be linked to North Korea's rocket man, Kim Jong-un, targeting organisations in the think tank sector.
TA427 sent a meeting request from a spoofed sender and launched a brief conversation "to engage the target and build trust". Afterwards, victims were directed to a dodgy site and convinced to run a PowerShell command.
During one incident, the command launched a multistage chain that executed PowerShell, VBS, and batch scripts, before unleashing QuasarRAT, which Proofpoint described as a "commodity malware also seen in cybercriminal activity."
In February 2025, TA427 posed as a Japanese diplomat and emailed a target requesting a meeting with Ambassador Shigeo Yamada at the Japanese embassy in Washington DC.
The initial message included a attachment titled Letter from Ambassador Cho Hyun-Dong.pdf, with the subject “[Japanese Embassy] Meeting Request.” Later emails reached the target’s personal and work inboxes, leading to a follow-up with a malicious PDF named after the target.
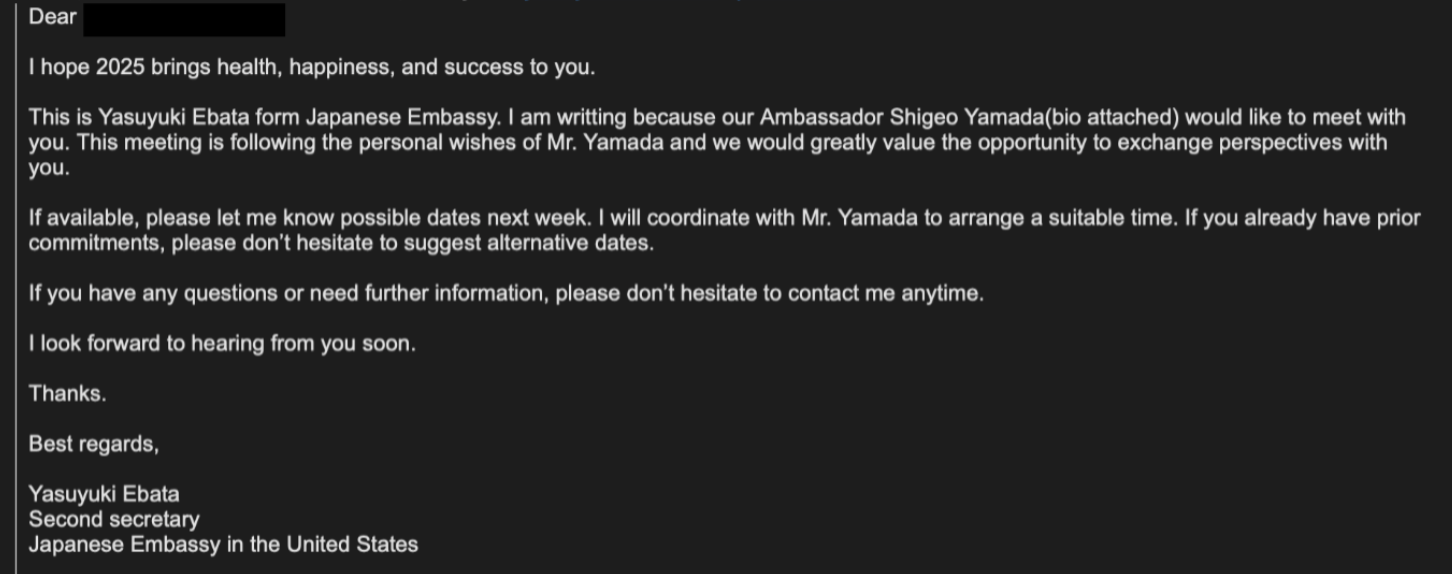
The file linked to a landing page on a dynamic DNS domain, spoofing a secure drive and hosting a fake file called Questionnaire.pdf. Download attempts then prompted a “register” popup and a second dialogue containing a PowerShell command:
This script downloaded a second-stage payload and launched Questionnaire.pdf, which was themed around Japanese nuclear policy.
Next, two scheduled tasks were created: one ran a VBS script every 19 minutes; the other every 20.
"However, this [second] VBS script did not exist, and the purpose of this task is unclear," Proofpoint explained.
Whilst the Japan attack did not execute further than running these tasks, another chain in January 2025 "followed a very similar path but with additional steps".
"In this case, the first scheduled task ultimately downloaded two batch scripts, which created and decoded two new PowerShell scripts and an obfuscated payload," the security firm added.
The attack chain ended with the unleashing of QuasarRAT - a tool TA427 has been known to use for four years.
"The second batch script executed the newly created PowerShell scripts to ultimately decode a Base64 and XOR-encoded QuasarRAT payload that communicated with the command and control (C2) IP address 38.180.157[.]197 over port 80," Proofpoint continued.
Microsoft has also observed a ClickFix infection chain variant using a URL to register a device and run PowerShell commands.
What about Iran and Russia?
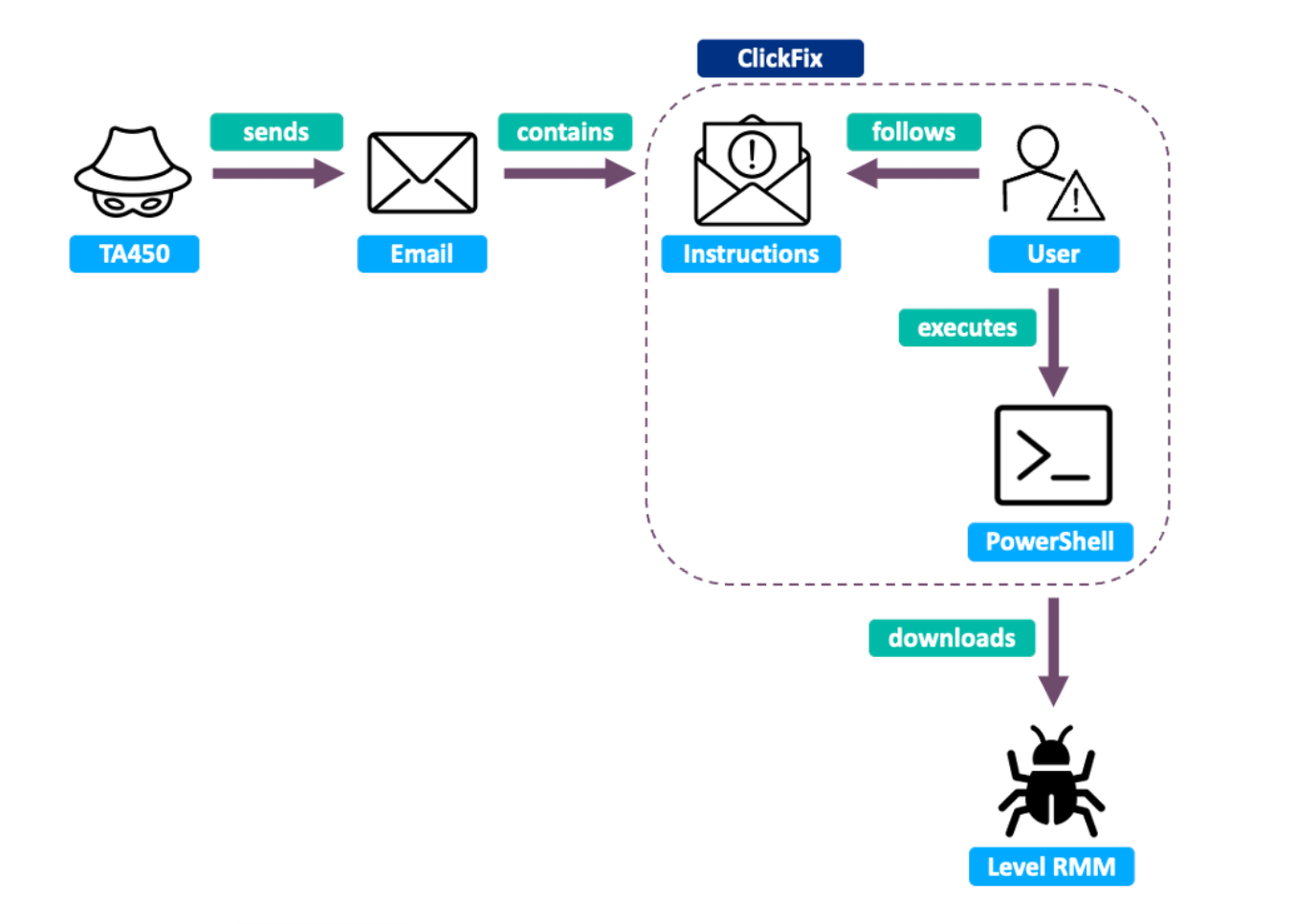
In November 2024, an Iranian group called TA450 sent an English-language phishing email to at least 39 organisations in the Middle East, which claimed to be from Microsoft and said: "Urgent Security Update Required – Immediate Action Needed."
"The attackers deployed the ClickFix technique by persuading the target to first run PowerShell with administrator privileges, then copy and run a command contained in the email body," Proofpoint wrote.
"The command was responsible for installing remote management and monitoring (RMM) software – in this case, Level – after which TA450 operators will abuse the RMM tool to conduct espionage and exfiltrate data from the target’s machine."
The Israeli National Cyber Directorate first reported the use of Level.
"While Proofpoint has observed TA450 historically using several RMM tools, such as Atera, PDQ Connect, ScreenConnect, and SimpleHelp as a foothold to conduct intrusions, this was the first sighting of Level in Proofpoint data," the security firm added.
Researchers said TA450 targets were "distributed primarily across the Middle East with an emphasis on the UAE and Saudi Arabia", but there were also global operations. Sectors including finance and government were the most popular targets.
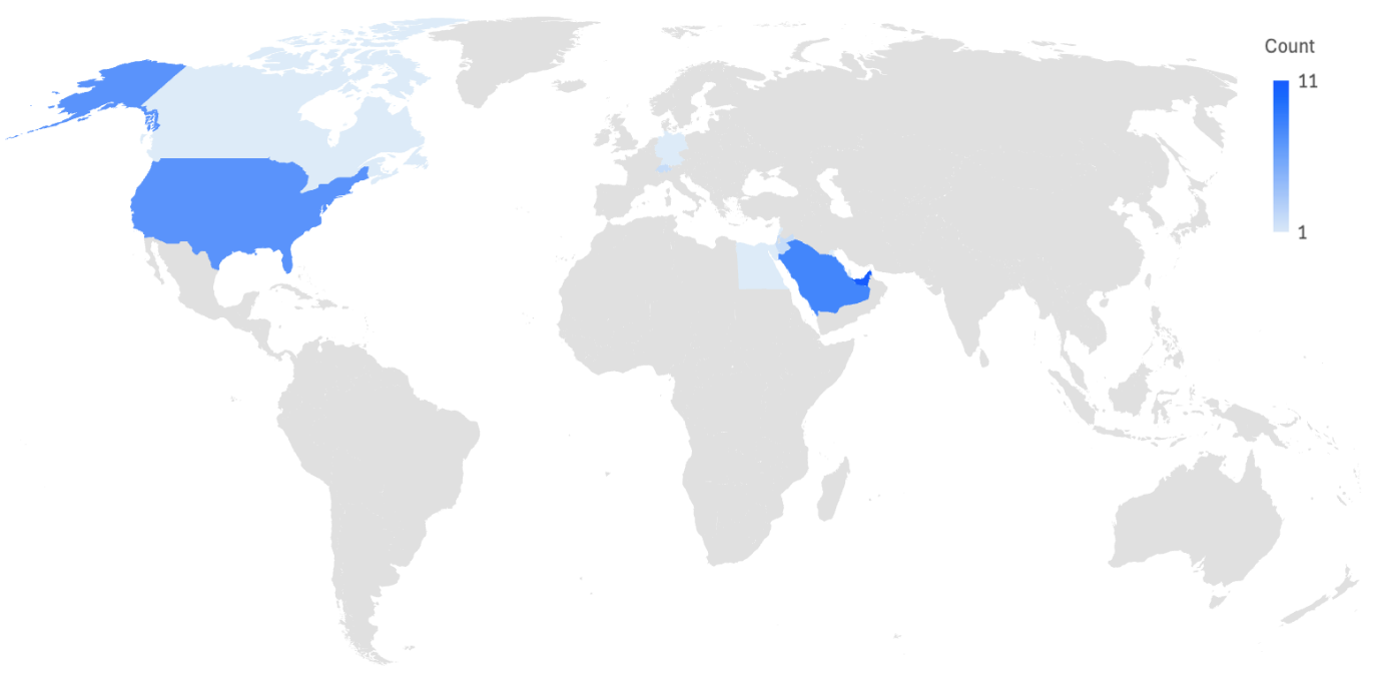
A group called UNK_RemoteRogue, which is believed to be Russian, has also been spotted deploying Clickfix, using compromised infrastructure to target two organisations linked to "a major arms manufacturer in the defence industry". A Moscow-linked gang called TA422 is believed to have launched similar attacks.
Additionally, Proofpoint said there is a "high probability" that threat actors from China have also experimented with Clickfix.
"As with other criminal – and often creative and novel – techniques, state-sponsored actors observe and emulate other groups (sometimes with a convenient byproduct of muddling attribution)," it wrote.
"Multiple examples of state-sponsored actors using ClickFix have shown not only the technique’s popularity among state actors, but also its use by various countries within weeks of one another."
Have you got a story or insights to share? Get in touch and let us know.




